Dabhi Manishaben Dahyabhai
Smt.B.K.Mehta I .T Centre Palanpur-385001 India
Article Publishing History
Article Received on :
Article Accepted on :
Article Published : 13 Dec 2014
Article Metrics
ABSTRACT:
Directive Access control system provides protected information with storage facility. This information can be shared among other connected or connectionless system. It is designed for the automation of time and attendance of authenticated or unauthenticated employee/visitor using RFID technology. Each Employee has RFID tag which carries his/her personnel recognition information. When these tags pass through the reader mounted at the specific division’s magnetic door, it generates interrogation field, they transmit information back to the Reader, thereby identifying them, attendance is recorded and access gates are opened, so the system monitor the movement of employee and record their real time data in a Time-stamp, which provides real time employee’s record like attendance, authorized and unauthorized entry in division, and visitor’s database with their purpose. The proposed RFID system’s objectives are to make automatic effective and efficient system so the administration time can be effectively reduced.
KEYWORDS:
RFID; Passive and Read/write tags; Reader module; Barcode technology; Directive access control system; Time-stamp
Copy the following to cite this article:
Dahyabhai D. M. Directive Access Control System. Orient.J. Comp. Sci. and Technol;7(3)
|
Introduction
Automatic recognition of objects by using electromagnetic fields is the main objective of RFID technology. Radio frequency identification is reliable and cost effective technology used for the personal identification, asset management, secure access, inventory control and numbers of sophisticated applications. Due to quicker performance, lower implementation costs and developed emerging standards causes. RFID was first used in the World War II by the British Air Force to differentiate allied aircraft and enemy aircraft. This paper focuses on implementing the automation of time and attendance using the RFID technology. Radio frequency waves are electromagnetic waves characterized by their frequencies used in radio communication. RFID is a technology used for product identification, locating assets, and people. It is used to identify and track with real-time information. It overcomes the boundaries of other identification tools which use light to communicate such as infrared and bar code technology.
Generalized RFID System
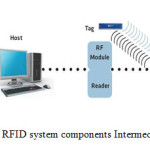
RFID system consists of transponders (RF tags), readers and backend system used for further processing of the acquired data. RFIDTransponder will identify itself when it detects a signal from a compatible Reader. Basic system components are shown in Figure (1). RFID tags are attached to objects; tag carries information such as a serial number, model number or any other imaginable data. As RFID Tag pass through a field generated by a compatible Reader, it transmit this information back to the reader. The system is provided with Application-Specific Software for certain window services.
RFID Tags (Transponders)
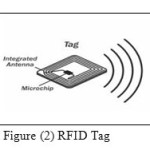
RFID tag is a small device equipped with a microchip which carries data and an antenna. Tags may be read-only (passive) or read/write (Active Tags). Read-only tags are most like barcodes, operates without a power supply and are less expensive, a shorter read range and have longer life than read/write tags. The encoded data cannot be changed, it just like serial number that is used to retrieve additional descriptive data such as item type, date of manufacture etc. Read/write tags utilize the energy from the radio beam of a RFID reader to get enough power to carry out simple calculations and respond with is normally a unique number. The unique number is to be standardized and stored in a central database, which will provide instant access; they can be rewritten and updated an unlimited number of times, and may offer “locked” sections that cannot be altered .Active tags have their own expensive power source, so have longer ranges, more memory, bigger in size and more with an application. Readers may be hand-held or mounted in strategic locations so as to ensure that they are able to read the tags, as the tags pass through an “interrogation zone.”The interrogation zone is the area within which a reader can read the tag. Reader contains internal storage, processing power, or an interface to back-end databases to provide additional functionality. Readers are designed in different sizes and shapes. Each Reader manufacturing company has its own set of standards and functionalities based on customer’s requirement. These devices handle Radio communication through the antennas and pass the tag information to the outside world. The reader attracts the data from passive tags by releasing radio frequency waves; but with active tags, the data is sent to the reader by the RF wave it releases from itself. In proposed system Readers uses tag contents as a look-up entry into a time stamp with employee’s information.
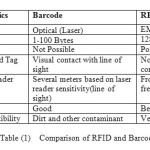
(1) Following table illustrates the main differences between competitive Barcode and RFID Technologies.
Dacs Overview
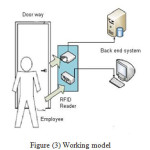
DACS is a generic application design to computerize and augment the labor-intensive work of recording and reporting in real-time with secure access in institution. The basic working model is illustrated in Figure (3).
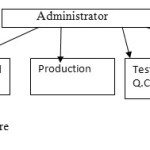
The proposed system have total four divisions with Administration as a master and the others i.e. Research & development, production, maintenance, testing & Quality Control as a slaves are considered. Every division has a magnetic door with RFID reader which is accessed with concerned RFID Tag. The Master (administrator) has RFID tag with full access i.e. access of all the divisions, while all slaves with RFID tags have limited access i.e. their own division only. The typical application structure with specific section is illustrated in Figure (4).
The Master module is responsible for reader management, user management and data management. The master has the highest privileges. It does the following Directive tasks
- Registering a new user
- Tag registration
- Access point configuration
- Issuing/ Canceling an ID card
Employee of one division required to access the other division for co-operative task than employee has to obtain the permission from the master for exact duration For visitor’s visit, he/she gather the visitor RFID tag of concerned division for exact duration. Sometimes it is necessary to open the particular division on the holiday to complete the delayed work than employee obtain the permission from the master and the other division remains closed. Time–stamp is maintained in the database, which contains timely information of the Tag’s Enter/ Exit. From this arrival time, stay-in time, departure time, other division time of the employee with specific division, division wise visitor database. Time-stamp is used to create attendance record and leave record. It may be used in account to calculate the pay-roll of the employee based on their overtime. From this database Master can supervise and evaluate the associated work of the division and individual employee.
 
Processing
- Attendance marking of employee.
- Calculate stay in time of Employee.
- Marking unauthorized and authorized other division entry
- Division wise visitor’s data base
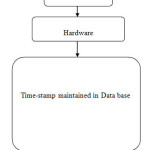
The control module reads input from the hardware. The RFID tag is read and a data log is maintained in the Time-stamp. This record is forwarded for central processing and storage as recorded data base reports. Flow diagram of proposed system is illustrated in Figure 5.
System Hardwar
In DACS each division has magnetic door with RFID reader module, which is communicate with central processing unit to maintain the database in back end system. The administrator act as a master module has privilege to supervise the activity of remaining slave modules. Every employee has RFID tag, which contain identity information.
Application Principle
The application consists of five main modules, as follows:
Scanning Input from Reader Module
Reader attached at the magnetic door reads the unique 10 digit (40 bit) serial number of tag within its field. So, when the Tagged user passes the Reader generated electromagnetic field, it sends unique information, and real time data is stored in the in the database. In general an application program gets the Reader ID and then receives Tag’s unique serial number from the employee. On the basis of comparison the system maintains real time data in Time-stamp.
Windows Service
Windows Service is created and used to avoid Human Intervention in the System. It provide us facility to create running executable applications that run in their own windows session, it can also has the ability to start automatically when the computer boots and also can be manually paused, stopped or even restarted. This makes services ideal for use on a server or whenever long-running functionality is needed.
Marking Attendance and Unauthorized Database
Attendance of employees is recorded on the basis of in time, stay-in time & out time in time-stamp. From this database total stay in time for each employee is generated. Attendance of those employees are not present is marked as “Absent‟. If the unregistered tagged employee try to access the division are marked as unauthorized, thus avoids the congestion and security related issues. Unauthorized tag data base is also maintained in time-stamp.
Authorized other Division Database
Most tasks are interrelated so employee of one division needs help or information from the other division so he/she has to obtain the prior request of other division access with purpose from master. The master authorized his/her RFID tags for other division for the fixed time. So he/she can access the magnetic door of the other division with their RFID tag. Authorized other division access data base is maintained in time-stamp.
Division Wise Visitor’s Data base
In industrial environment many outsiders like marketing executives, raw material suppliers, customers etc. have to visit the specific division of the organization as per their need. In such cases the visitor get the visitor RFID tag of the concerned division from the reception after registration and get the access permission of specific division’s magnetic door for predefined time from master. So division wise visitor database is maintained in time-stamp. It contains number of visitors visited in organization and specific division, with identification and purpose.
Conclusion
RFID is a technology of Automatic Identification and Data Capture (AIDC) technologies, which is more mature than barcode, optical character identification and infrared identification systems. The paper proposed a novel usage of RFID systems in institution Directive administration. It is more mature in many applications and supported by current and evolving standards. RFID can be used to improve accuracy, speed and responsiveness. Most organizations are implementing RFID systems and we hope that the fundamental of this paper will also contribute towards its development in industries/organizations where issues like specific division access, attendance, and supervision of employee are highly critical and also affect employee’s effectiveness.
The administrator is always concerned about their employee’s presence in his/her owns divisions as well as the other divisions, with the prior permission. The system automatically generates total time–stamp of the individual staff as well as the particular division. It also generates the time report i.e. when the particular task assigned to the concerned employee and when it is completed, based on this evaluation the administrator decides the further increment/promotion. The system generates the database of number of visitors visited with purpose to the organization and division with time–stamp.
References
- A Policy based access control mechanism for RFID Information services.
- Automation of time and attendance using RFID systems. By Aysha Qaiser and Shoab A Khan, Fatima Jinnah Women University, Rawalpindi, College of EME, NUST
ByZ.Li,C.H.Chu,W. Yao, wxy119@psu.edu.
- Master Thesis: “Theoretical and Experimental Investigation of Impact of Automatic Healthcare & Automotive Industries in Iran.” By Saram Tofighi Edalatkhah, Tarbiat Modares University Faculty of Engineering, Dept of Industrial Engineering,Lulea University of Technology.
- RFID Based People Management System Using UHF Tags Sourish Behera & Rajesh Kumar Kushwaha proceedings of ASCNT – 2009, CDAC, Noida, India.
- RFID Handbook by Klaus Finkenzeller, John Wiley & Sons, 2003.
- RFID Security by Prof. Dr. Heiko Knospe, University of Applied Sciences Cologne, E-mail:heiko.knospe@fh-koeln.de Prof. Dr. Hartmut Pohl, University of Applied Sciences Bonn-Rhein-Sieg, E – mail:Hartmut.Pohl@fhbonn-rhein-sieg.de, JISC Technology and Standards Watch, May 2006.
- Security and Privacy Aspects of Low-Cost Radio Frequency Identification Systems. Stephen A. Weis, Sanjay E. Sarma, Ronald L. Rivest and Daniel W. Engels. Laboratory for Computer Science Auto-ID Center, Massachusetts Institute of Technology, Cambridge, USA.
- Smart attendance system by using RFID, M. K. Yeop Sabri, M. Z. A. Abdul Aziz, S. R. Mohd Shah, M. F. Abd Kadir, Fakulti Kejuruteraan Elektronik dan Kejuruteraan Komputer, niversiti Teknikal Malaysia Melaka, Karung Berkunci 1200, Hang Tuah Jaya, Ayer Keroh, 75450, Melaka, Malaysia.
- What is RFID? Research Note by Gartner Group, 1 September 2000.
- White paper of ABC’s of RFID:Understanding and using radio frequency identification,
- White paper: Introduction to RFID, Frequency Ware Inc. Canada, Email: info@frequencyware.com

This work is licensed under a Creative Commons Attribution 4.0 International License.