Vaishali Mishra¹, Suhas Patil² and Ashutosh Mishra³
¹Vishwakarma Institute of Information Technology, Pune (India)
²Bharati Vidyapeeth University COE, Pune (India)
³Vishwakarma Institute of Information Technology, Pune (India)
Article Publishing History
Article Received on :
Article Accepted on :
Article Published :
Article Metrics
ABSTRACT:
The introduction of personal computing and wireless communication technology provides an option for on site device software updating and data retrieving. This is especially true for any devices sitting in a remote site where computing network is not accessible. In many advanced computing systems, frequent software updating and configuration profiles refreshing are required. This is clumsy and error prone procedures when users are not familiar with the operating systems. Suppose all the necessary files and programs are predefined in a mobile phone. All necessary files and software can be transferred to the corresponding computing devices and PCs at remote sites through wireless communication links such as Bluetooth/infrared. This idea helps to solve the initial installation cost of a communication network to a remote site. Index Terms - Bluetooth, mobile communication.
KEYWORDS:
Cell phone; portable storage device
Copy the following to cite this article:
Mishra V, Patil S, Mishra A. Cell Phone as a Portable Storage Device and Beyond. Orient. J. Comp. Sci. and Technol;1(1)
|
Copy the following to cite this URL:
Mishra V, Patil S, Mishra A. Cell Phone as a Portable Storage Device and Beyond. Orient. J. Comp. Sci. and Technol;1(1). Available from: http://www.computerscijournal.org/?p=2031
|
Introduction
In existing network conditions, different kinds of connection sessions are available for today high speed network operation. The examples of these network sessions are client to client sessions, client to server sessions, peer to peers sessions, and so on. There are differences among these methods of network session operations.
Regarding the remote session, the remote desktop from microsoft windows performs similarly to the client-client sessions. With remote desktop on windows XP Professional, you can have access to a Windows session that is running on your computer when you are at other computer. This means, for example, that you can connect to your work computer at home and have access to all of your applications, files and\network resources as though you are in front of your computer at your office. You can leave program running at work and when you get home, you can see your desktop at work displayed on your home computer, with the same programs running. When you connect to your computer at work, remote desktop automatically locks that computer so no one else can access your applications and files while you are gone. When you come back to your computer at work, you can unlock it by typing CRTL+ALT+DEL. Remote Desktop also allows more than one user to have active sessions on a single computer1,2. This means that multiple users can leave their applications running and preserve the state of their Windows sessions even while other are logged on. Remote Desktop allows ore people in an organization to take advantage of the flexibility provided by a distributed computing environment.
With fast user switching, you can easily switch from one user to another on the same computer. For example, suppose you are working at home and have logged on to the computer at your office to update an expense report. While you are working, a family member needs to use your home computer to check for an important email message. You can disconnect Remote Desktop, allow the other user to log on, and check mail, and then reconnect to the computer at your office, where you see the expense report exactly as you left it. fast user Switching works on standalone computers and computers that are members of workgroups. Remote Desktop enables a variety of scenarios, including:
- Working at home – Access work in progress on your office computer from home, including full access to all local and remote devices.
- Collaborating – Bring your desktop to a colleague’s office to debug some code, update a presentation, or proofread a document.
- Sharing a console – Allow multiple users to maintain separate program and configuration sessions on a single computer, such as at a teller station or a sales desk.
Many remote desktop and terminal server, connections provide clipboard sharing, allowing you to cut and paste from programs running in your remote desktop session to programs running on your local computer. When you cut or copy information from a program, it is moved to the Clipboard and remains there until you clear the clipboard or until you cut or copy another piece of information. The clipboard window in Clip book Viewer shows the contents of the Clipboard. You can paste the information from the Clipboard into any document as often as you like. However, the information is only stored on the Clipboard temporarily. The shared clipboard synchronizes its contents with the local clipboard. You can copy and paste text or graphics from a document within the remote desktop connection window, and paste it into a document on your local computer.
Using these traditional techniques has several limitations. The major problem faced is the mobility of the data, compatibility of devices, and
last is the problem of security. A solution to the problem of mobility is suggested. A mobile phone is now a very familiar device to most people but not
everyone really knows about the advanced functions and capabilities incorporated in the mobile phone.
Not many people are aware of all the metamorphoses the mobile phone has undergone before becoming what it is today. The Bluetooth technology is much popular for transmitting data over a short range. In this paper, we are attempting to replace USB drives with a mobile phone and beyond. .
Bluetooth
One of specifications of Bluetooth Technology is the introduction of various “profiles” of Bluetooth [3]. Why does the Bluetooth SIG have to introduce the concept of profiles? Nowadays, there are a number of networking standards including Ethernet, TCP/IP, and PPP. All of these standards can only apply to computers. However, the application of Bluetooth Technology will not be fixed inside computers, devices like earphones, printers, digital cameras, mobile phones, and even refrigerators, would be implemented with Bluetooth in the future. Bluetooth has developed its own communication protocol, inquiry and page signal4, 5.
As a result, we can foresee that Bluetooth would not be fixed to be used in an operating system and application software as it’s nowadays for TCP/ IP. Thus, it is necessary to define the operational mechanism, specified variables, hopping sequences and work distribution of each device for
each case of application of Bluetooth, these sets of definition are the profiles of Bluetooth. The aim of introducing the concept of profile is to increase
the interoperability between devices with Bluetooth, so that devices from A company would be able to communicate with devices from B company. In
different scenario, different profile would be applied to different configuration files in order to get the subsection best solution for the responsible devices.
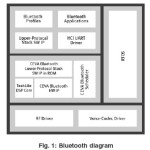
A generic access profile block diagram is shown in Fig.1. This gives the Bluetooth the interoperability among different computing platforms and operating systems.
Operation of updating configured files in a foreign client pc. The Bluetooth module used in the test is the GW- BHOZU USB adapter from PCI.
The reason to choose this is that it can support operating systems from Windows 98 SE to Windows XP (Windows 98 not supported, since
there’s no USB support before Windows 98 SE), while PCI is one of the well known manufacturer in networking devices.
Following operations are suggested
File transfer service in bluetooth device
The file transfer service allows one Bluetooth device to perform file operations on the default file transfer directory of another Bluetooth device in the foreign client PC.
Perform an operation on a folder or file
In the foreign client PC, which will use the File Transfer service, the following steps are performed
- In the folders pane of My Bluetooth Places, select Entire Bluetooth Neighborhood.
- In the right pane of Entire Bluetooth Neighborhood, right-click anywhere except on a device name and select Refresh from the pop-up menu.
- In the Folders pane of My Bluetooth Places, right-click the device you want to Transfer Files with and select Discover Available Services from the popup menu to update the available services ist. The available services will be displayed in the right pane of My Bluetooth Places.
- Still in the Folders pane of My Bluetooth Places, click the plus (+) sign in front of Public Folder to expand that folder. If there are additional folders inside the expanded folder then those additional folders may have to he expanded. Folder contents are displayed in the right pane of My Bluetooth Places.
Types of file transfer operations
In the right pane of My Bluetooth Places, right-click a folder item and select an option from the pop-up menu. A dialog box (the title vanes, depending on the operation being carried out) appears and the status line (bottom of the dialog box) indicates the operational step that is being carried out. The types of operations that can be accomplished are:
Open
- Files are opened in the application associated with them.
- Folders are expanded to show their contents.
Print
Sends the selected server file to the client default printer.
Send to
- 3.5″ Floppy Drive: copies the selected item(s) from the server to the client 3.5″ floppy drive.
- My Shared Folder: copies the selected item(s) from the server to the default File Transfer folder on the client.
Copy
Copies a folder and its contents, or individually selected files in a folder, to the Windows clipboard.
Delete
Deletes selected file(s) and/or folder(s) on the server.
Rename
Allows you to change an empty folder name.
Properties
Displays the file or folder properties dialog box.
The process can be performed by handheld devices operating on wireless Bluetooth interfacing.
Why bluetooth
The biggest advantage that Bluetooth has over IR is that one device doesn’t need to be in the line of sight of the device that it’s communicating with, so it can work through walls and floors. For example, with IR, if somebody walks between your TV set and remote control, the beam is broken andthe transmission is lost until the obstruction is removed. Not so with Bluetooth.
Basically what this means is that Bluetooth devices randomly change frequencies (between the 2.40 and 4.48 GHz range) over a thousand times per second, using 79 different channels within the spectrum, so even on the chance that two devices hit the same exact frequency, the disruption will be negligible.
Another cool-feature of this technology is that Bluetooth-enabled devices can find each other without the user’s having to do anything. For example, when two Bluetooth devices come within range of each other, they immediately begin a series of negotiations to determine if they have data to share or need to make a connection, and then they form a small network known as a piconet or a personal area network (PAN for short).
Conclusion
The setup of a client PC or sever PC can be time consuming and, in most cases, it is some error prone operations. If these procedural activities can be performed by an experienced engineer, many of the unnecessary errors can be eliminated and solved. With the available wireless technology and abundant networking facilities supported for PCs connected through computing network, these operations can be done in a simple and organized manner through a handy computing devices. The concerned device configuration files and data validation files can always be updated through
mobile communication network to the handheld devices, which is used to update the target foreign PC.
Although originally intended to be a modest communication terminal, the mobile phone has unexpectedly evolved to become an inseparable companion of every people. Mobile phones contains more and more memory . The mobile phone will have more functions and play many more roles as personal data storage, portable storage in addition with MP3 player,camera,etc.
References
- Windows XP Networking Features and Enhancements, Microsoft Technical Article, (2002)
- John Calboon, “Mobile Computing with Windows XP”, Microsoft Technical Articles, (2001).
- Specification of Bluetooth System Volume 2, Profiles, Bluetooth SIG.
- Brent A. Miller, Chatschink Bisdikian, “Bluetooth Revealed”. Prentice Hall 2nd Edition.
- D.Kammer, G.McNutt, B.Senses, J.Bray, “Bluetooth Application Developer’s Guide: The Short Range Interconnect Solution”. Syngress Publishing Inc., (2002).

This work is licensed under a Creative Commons Attribution 4.0 International License.