Introduction
Blood loaded with oxygen comes into the hands through the arteries, and then again towards the heart through the veins. The oxygen depleted blood is not the same as the absorption filter arterial it absorbs light at wavelengths near infrared (about 760 microns).
When the hand is illuminated with infrared light, the vein appears black. It is recorded as an “identity card” in a database and can then be used for comparison during authentication.
There are two types of “photography”. Method “reflective” is more reliable than the transmission method (capture of light that passes through the hand). Indeed, when it is cold, the veins contract and the contrast is not quite visible transmission. For cons, the reflected light is not changed, and can use the same method reflective cold weather. On the other hand, the two parts of the device are in the same location, since the light is returned.
There is noway tocheat,because theycannot “shoot” the veins of thehand.The vascular network isunique to each individual: even identical twinsaredifferent.According to Fujitsu, which compared 140 000palms, TFA -False Acceptance Rate(people authenticated as some one else)is less than0.00008%. There isno contactduring authenticationaswith fingerprints, so no hygiene problem. However, the method is stilltoo recent to beproperly assessed.Thescanneris relatively bulkycompared tofingerprint sensors.
As often noted in the literature, hand shape biometrics is attractive due to the following reasons:
- We do not need to record photography: respect for privacy,called “traceless” 1-2.
- Readersof biometricsvenous systemeven work withstained hands3.
- High level ofsecurity,to date nomeansto defraud4-5.
- FAR – False Acceptance Rate (people authenticated as someone else) is less than 0.001%6-7.
- Durable: Do not change in time, unlike the way or face or iris.
Operation of a hand veins-based biometric system
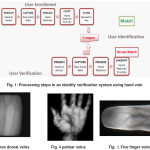
The biometric system has two purposes: authentication and identification.
Authentication or verification
It is better known amongst 1.1 8, because it allows to certify (ensure) a claimed identity of the user9.
Identification
It is better known one amongst N8, since it allows users to determine which best fits the person to recognize. It adds the ability to check whether the user actually belongs to the database.
Based on the comparison result, the claimed identity is accepted or denied. The identification system includes the following modules: the sensor module, the feature extraction module, the matching module, the decision-making module and an optional template adaptation module.
The sensor module
In visible light, the veins are not apparent. Indeed, a multitude of other factors, including the surface characteristics such as moles, warts, scars, pigmentation and hair can also hide the image9. Fortunately, the use of the infrared light eliminates most unwanted surface features.
Required parameters to obtain good quality data are listed below10-9.
- The light affects the quality of the image obtained with the exception of no IR filter.
- The temperature of the ambient environment must be neither too hot nor too cold, around the human body temperature.
- The distance between the sensor and the object should be sufficient for a good acquisition.
Starting with Jackson W. Wegelinpatent11, ncludes a dispenser controller coupled to a memory unit, which includes a database of previously-stored vein patterns. A vein-pattern sensor maintained by the dispenser images the unique vein pattern of a user’s hand without contact. A recent study proposed using a three dimensional biometric scanner1 for the capillary mapping of the palm of the hand2 incorporates two image sensors5,6 configured for obtaining a stereoscopic image of a vascular map and where for each image corresponding to each wave length, the depth of each point on the plane is known12.Some multimodal biometric systems captureplamprint/ finger vein15, hand geometry/vein16. Other systems capture the palmar veins13-14. Based on On registering finger vein information, a hand photography camera 106 photographs an image in a state where a finger is set to a finger vein reader 102, and it is discriminated of which finger the finger vein information is to be registered, on the basis of the photographed image. There is too central combining several modalities as17 which comprise a central command station (9) in signal communications (24a, 24b, 24c) with a series of blasting machines (16a, 16b, 16c). Command station9 has a biometric analyser unit10 and a authorizing means11. The blasting apparatuses have enhanced security features by including biometric analysis of specific biological features13 of an authorized blast operator to generate a known biometric signature. The biometric signature can be derived from a fingerprint scan; a recognition scan of a hand, a foot, an iris or a retina; a skin spectroscopy analysis; a finger vein pattern analysis; a voice recognition analysis; or a DNA fingerprint analysis.
The feature extraction module
In order to segment, improve the quality of the image, extract veins from hand, we need some techniques:
Format conversion JPEG BMP
The conversation JPEG BMP is required. Indeed, the main advantage of BMP image quality is provided as BMP format is not compressed and therefore no loss of quality. Against by the JPEG format is compressed and therefore quality lost18.
Enhancement
The resulting image may not contain noise as tasks, blobs, dust … ect. Different filters can be applied to eliminate the noise and enhance the image, but if the pictures have a good quality, this step is not required19. In20, the clearness of the vein pattern in the extracted ROI varies from image to image; they uses a 5×5 Median Filter to remove the speckling noise in the images and a 2-D Wiener filter to the ROI image to suppress the effect of high frequency noise21. Uses a various contrast enhancement techniques in order to compare which gives the best results, the study is very interest.
Converting the color image into a gray level
Converting a color image into a grayscale means that the image size will be reduced from 24 bits per pixel (color image) to 8 bits per pixel (grayscale image) 22-23. Instead of having three matrices that represent the level of colors (red, green, blue) for each pixel, we have just a single matrix that represents the gray level for each pixel, which reduces the processing time24-25.
Binarization
Binarization is the segmenting the image into two levels; object (hand region) and background; most of the time the object segment which is the region of interest (ROI) in white and the background segment in black26-28.
Feature extraction
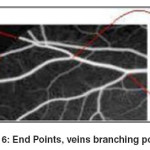
After the binarization, there is the most difficult step which is the feature extraction. Some researchers add a step in this module29-32. Some works uses the minutiae features extracted from the vein patterns for recognition, which include bifurcation points, ending points and the position and orientation of minutiae points33,35,36,37. Uses it with the vein finger, when [34] uses it with the dorsal hand vein. In38 the feature extraction was based on the geometry veins.
The figure below shows these minutiae (playback direction: from left to right).
We can call it too Identification/Authetication phase or then Verification. The image of the veins that was extracted in the previous phase allow us to create a database of prototypes with (s) models that are in the base (template) byAuthenticating the identity of an undividual, will either accept the person, or reject it. Instead of the identification, the system will identify the right person. In order to evaluate theirsystem testing performance39, uses a dataset of 500 persons of different ages above 16 and of different gender, each has 10 images per person was acquired at different intervals, 5 images for left hand and 5 images for right hand. [40] used correlation and template matching as a recognition algorithm whether41 used Using Principle Component Analysis (PCA).
Survey : biometrics dorsal veins
This last year’s many works has been made on the dorsal veins, the table below give the several techniques that has been used for each biometric step.
Thresholding (removing noise)
In [42], they used the low pass Gaussian filter (3 * 3) and high pass (11 * 11) to obtain a good image vein patterns. Others have preferred to use the Median filter (5 * 5) instead of Gaussian43,45,49 in the case of 45 the Gaussian filter remove some needed edges, as an alternative the Median filter that conserves the edges49.
On the other hand, 44,42,57 used the two filters: low pass Gaussian components to reduce the image having a high frequency (dark pixels) and Median (5 * 5) to remove speckles (the small jobs that appear in the image texture ). Another technique has been adapted in58; the ridgelet transform in order to eliminate noise and highlight the veins.
In [48],they used Match filter, Wiener filter, smoothing filter to eliminate noise and get clear veins.
Binarization
Several techniques exist for the binarization. Indeed42-45,47,48,56,used a local thresholding based on the neighboring pixels, as it gives better results compared to theglobal threshold8,11 have used another type of automatic thresholding is OTSU, for it requires shortprocessing time59.One more method of binarization, is the K-means which was applied with k = 2 (the bottom and hand)55.
Feature extraction
Some researchers divide this module in two steps extraction veins then extracting minutiae; sometimes we can found onlyfeature vein’s extraction.
Extraction veins
The local thresholdinggives good results; for that it is very used in particular in30,42,44,45,50,51,52,53,56,43. Applied the wavelet transformation to locate veins. Others used a quadratic function46, for the reason that it has as main advantage reducing the size of the matrix; which has a direct impact on the processing time classification46-47. Used OTSU method which has been widely used for the document’s binarization; it often gives the best results and the fast20. UsedCholesky decomposition and Lanczos algorithm to reduce the processing time. When,53 based on anhistogram equalization;this makes dark pixels appear darker and bright pixels appear brighter. To get the right threshold from the histogram.
Extraction of minutiae
Crossing number used to extract more properties on the veins29,30,60,28. used Hough transform to isolate the end points that will be used afterwards for classification54.
Classification
To compare the shape of the extracted veins (s) size (s) of reference44,56,31,30 used the Hausdorff distance, the test results showed that all the vein pattern images in the database have been correctly recognized44,46,47,50. Used Euclidean distance, the error rate of FAR and FRR was still reduced.
Others51 have used the method of minutiae triangulation, which can form triangles from minutiae (bifurcation points and end points). Then a score is generated by computing the number of triplets bifurcation and end points of the input image, and compared with the number of the triplets and end points that are stored in the database. Another technique was used, the rigid registration51, which showed that the right hand and the left hand of the same person are not identical. 4.3.1. Survey : palm vein biometrics In the followed table, we quote some works that have been studiedaround the palm veins. The boxes marked with / want to say that the technique was not mentioned in references In61, the filter-GSZ shock was used to eliminate noise and improve contours62-63. Used the Gaussian filter to correct the contrast of the image63 used the Gaussian filter for high pass intensity improvement.
In61, they based on the Gabor filter to extract the characteristics of the hand in the form of texture. Others have preferred to use a local thresholding”SIFT”. In62 extract the hand and palm vein doing like65, and showed the effectiveness of this method for binarization. Another technique, which is the multi-level thresholding was applied in64.
In61, they used the Gabor filter to extract the veins, then they made a skeletonization to better visualize the veins.
In61, they used K-NN to classify individuals where63 used another technique which is the correlation coefficient; it is widely used in image processing. By cons64 adopted the method of TOH et al in66.
Enhancement
Used a filter oriented to improve the image46. In67, the median filter (5 * 5) was used to improve the image quality. Median filter and another Special (3 * 3) was applied after the detection of finger vein to eliminate all single points (unwanted noise in the background) from the image67. In68, they used the Gaussian filter to eliminate noise such as dust, the median filter for image binarization, and an iterative labeling connected components because the picture still contains points not belonging to the finger vein.
Binarization
In67, a threshold (= 0) was set to extract to the bottom. In68, they preferred to use an automatic thresholding, which gives good results, based on the pixel neighbors (more details are in67). Applied a mask in order to detect the edges of the finger, and they reduced the size of the image taking area of the finger69.
Vein Extraction
To extract finger vein, three algorithms were applied in66 are in38-40 respectively; whose goal is to apply the methods used in fingerprint to extract finger vein66 and see what happens. So, by combining several resolutions, the algorithm used in38 gave stable results for the FAR and FRR. In41, they made the veins in the form of a skeleton using a fairly simple and effective.
Found that the finger veins are not always clear, so the solution is to use the local binary pattern, because it is a very robust method. Then they45 classified the code that has been obtained by this method into three categories: LA (Large amount), MA (Medieum amount) and SA (Small amount) using SVM.La figure below shows it. Also, in45 they deduced that the minutiae extraction step is not necessary, it takes a lot more time in treatment. So they have to add this step.
Classification
In67 used the methods found in43-44. By cons69 used the Hamming distance based on the LBP code has been extracted in the extraction phase characteristics are.
Conclusion
In a biometric system, two important criteria to consider: the accuracy of results and processing time. It is for this reason that this chapter has presented a state of the art biometrics veins of the hand, to discover different algorithms and study them in detail in the chapters that come after, starting from the second step is preprocessing to the classification, which aims to identify people by the dorsal veins of the hand.
Indeed, the most important operation in the preprocessing module is the binarization. Several techniques existbinarization, but to choose a single technique that meets these two criteria, a state of the art must be done in order to know the complexity of each algorithm and the quality of the results provided.
References
- Hisham Al-Assam, Sabah Jassim, Security evaluation of biometric keys, Computers & Security, 31(2): 151-163 (2012), ISSN 0167-4048, 10.1016/j.cose.2012.01.002.
- Lakhdar.LIMAM,Lamine. HANINI, «Mise au point d’un système d’acquisition biométrique : SAB-11 Veines de la main,» PFE pour l’obtention du diplôme d’ingenieur en instrumentation,Institut de maintenance et sécurité industrielle, Université d’Oran,Algérie, 2011.
- Nicolás Antequera Diaz & José Sanchez Del Rio Saez, 3d biometric scanner, EP 2413263 A1, 2012
- Takahiro Aoki, Mitsuaki Fukuda & Soichi Hama, Biometric authentication device and biometric authentication method, EP 2371283 A1, 2011
- Ltd. IPO Tatsuyuki Hitachi Nakazawa, Ltd. IPO Kazuyuki Hitachi Yazumi, Biometric information registration apparatus, EP 1744264 A2, 2007
- Eiji Makimoto, Yasuo Mizuno,Kunihiro Nomura, Hisao Ogata & Noboru Takamura, Biometric Authentication Apparatus and Biometric Authentication Method, EP 2312495 A2, 2011
- Blayn W Beenau, David S Bonalle, Seth W Fields, William J Gray, Carl Larkin, Joshua L Montgomery, Peter D Saunders, Hand geometry biometrics on a payment device, US 8289136 B2, 2012
- Ronald Stewart, Security enhanced blasting apparatus with biometric analyzer and method of blasting, EP 2357442 A2, 2011
- Pal, M. M., & Jasutkar, R. W. (2012, May). Implementation of Hand Vein Structure Authentication Based System. In Communication Systems and Network Technologies (CSNT), 2012 International Conference on (pp. 114-118). IEEE.
- Wang, L., & Leedham, G. (2006, November). Near-and far-infrared imaging for vein pattern biometrics. In Video and Signal Based Surveillance, 2006. AVSS’06. IEEE International Conference on (pp. 52-52). IEEE.
- JAIN, Anil K. et KUMAR, Ajay. Biometricsof next generation: An overview. Second Generation Biometrics, 2010
- Wang, L., Leedham, G., & Siu-Yeung Cho, D. (2008). Minutiae feature analysis for infrared hand vein pattern biometrics. Pattern Recognition, 41(3), 920-929.
- Prasanna, R. D., Neelamegam, P., Sriram, S., & Raju, N. (2012). Enhancement of Vein Patterns in Hand Image for Biometric and Biomedical Application using Various Image Enhancement Techniques. Procedia Engineering, 38, 1174-1185.
- R.KAVITHA & al, « Localization of palm dorsal vein pattern using image processing for automated intra venous drug needle insertion,» International Journal of Engineering Science and Technology, vol. 3, n° %16, pp. 4833-4838, June 2011
- Loh Yee.KOON , «Implementation of hand vein biometricauthentification on FPGA-BASED embedded systèm,» thesis to obtain the degree of Bachelor of Engineering (Microelectronics), Faculty of Electrical Engineering, Universiti Teknologi Malaysia,… 2010.
- Wang, J. G., Yau, W. Y., Suwandy, A., & Sung, E. (2008). Person recognition by fusing palmprint and palm vein images based on “Laplacianpalm” representation. Pattern Recognition, 41(5), 1514-1527.
- Wang, M. H., & Chung, Y. K. (2012). Applications of thermal image and extension theory to biometric personal recognition. Expert Systems with Applications.
- Badawi, A. M. (2006, June). Hand vein biometric verification prototype: A testing performance and patterns similarity. In Proceedings of the 2006 International Conference on Image Processing, Computer Vision, and Pattern Recognition, Las Vegas USA.
- Wang, K., Zhang, Y., Yuan, Z., & Zhuang, D. (2006, June). Hand vein recognition based on multi supplemental features of multi-classifier fusion decision. In Mechatronics and Automation, Proceedings of the 2006 IEEE International Conference on (pp. 1790-1795). IEEE.
- Kumar, A., & Prathyusha, K. V. (2009). Personal authentication using hand vein triangulation and knuckle shape. Image Processing, IEEE Transactions on, 18(9), 2127-2136.
- Ajay KUMAR and K. Venkata PRATHYUSHA, «Personal Authentication using Hand Vein Triangulation and Knuckle Shape,» IEEE Transactions on Image Processing, September, vol. 18, pp. 2127-2136 , 2009.
- Peter Gregory, C. I. S. A., SIMON, Michael A., et al. Biometrics for dummies. For Dummies, 2008.
- Loh Yee.KOON , «Implementation of hand vein biometricauthentification on FPGA-BASED embedded systèm,» thesis to obtain the degree of Bachelor of Engineering (Microelectronics), Faculty of Electrical Engineering, Universiti Teknologi Malaysia,, 2010.
- M.M.Pal and W. R.Jasutkar, «Implementation of hand vein structure authentification based system,» BIOINFO Computer Engineering, vol. 2, n° %11, pp. 19-21, 2012.
- M.Rajalakshmii and R.Rengaraj, «Bimetric authentification using near infrared images of palms dorsal vein patterns,» International Journal of Advanced Engineering Technology , vol. 2, n° %14, pp. 384-389, October-December, 2011
- Malki, S., & Spaanenburg, L. (2007, May). Hand veins feature extraction using DT-CNNS. In Microtechnologies for the New Millennium (pp. 65900N-65900N). International Society for Optics and Photonics.
- Wang, L., Leedham, G., & Siu-Yeung Cho, D. (2008). Minutiae feature analysis for infrared hand vein pattern biometrics. Pattern Recognition, 41(3), 920-929.
- Miura, N., Nagasaka, A., & Miyatake, T. (2004). Feature extraction of finger-vein patterns based on repeated line tracking and its application to personal identification. Machine Vision and Applications, 15(4), 194-203.
- Jain, A., Ross, A., & Prabhakar, S. (2001). Fingerprint matching using minutiae and texture features. In Image Processing, 2001. Proceedings. 2001 International Conference on (Vol. 3, pp. 282-285). IEEE.
- Jain, A. K., Hong, L., Pankanti, S., & Bolle, R. (1997). An identity-authentication system using fingerprints. Proceedings of the IEEE, 85(9), 1365-1388.
- Wang, K., Zhang, Y., Yuan, Z., & Zhuang, D. (2006, June). Hand vein recognition based on multi supplemental features of multi-classifier fusion decision. In Mechatronics and Automation, Proceedings of the 2006 IEEE International Conference on (pp. 1790-1795). IEEE.
- Badawi, A. M. (2006, June). Hand vein biometric verification prototype: A testing performance and patterns similarity. In Proceedings of the 2006 International Conference on Image Processing, Computer Vision, and Pattern Recognition, Las Vegas USA.
- Tanaka, T., & Kubo, N. (2004, August). Biometric authentication by hand vein patterns. In SICE 2004 Annual Conference (Vol. 1, pp. 249-253). IEEE.
- Khan, M. H. M., Subramanian, R. K., & Khan, N. M. (2009). Low dimensional representation of dorsal hand vein features using principle component analysis (PCA). World Academy of Science, Engineering and Technology, 49, 1001-1007.
- Sang-Kyun.IM, Hyung-Man.PARK, Young-Wooang.KIM, S-Chan.HAN, Soo-Won.KIM,Chul-Hee.KANG,Chang-Kyung.CHUNG, «An biometric identication system by extracting hand vein patterns,» Journal of the Korean Physical Society, vol. 38, n° %13, pp. 268-272, March 2001.
- Biometric verification using thermal images of palm-dorsa vein-patterns Lingyu WANG, Graham LEEDHAM, «A thermal hand vein pattern verification system,» In Proceedings of ICAPR (2), pp. 58-69, 2005.
- Mohamed SHAHIN, Ahmed BADAWI, and Mohamed KAMEL, «Biometric Authentication Using Fast Correlation of Near Infrared Hand Vein Patterns,» International Journal of Biological and Medical Sciences 2:3, pp. 141-147, 2007.
- Maleika Heenaye- Mamode KHAN and Naushad Ali Mamode KHAN, «A new method to extract dorsal hand vein pattern,» International Journal of Computer Science and Information Security, vol. 6, n° %13, pp. 26-30, 2009.
- Ajay KUMAR and K. Venkata PRATHYUSHA, «Personal Authentication using Hand Vein Triangulation and Knuckle Shape,» IEEE Transactions on Image Processing, September, vol. 18, pp. 2127-2136 , 2009.
- Maleika Heenaye- Mamode KHAN , Naushad Mamode KHAN and Raja K.SUBRAMANIAN, «Feature Extraction of Dorsal Hand Vein Pattern using a fast modified PCA algorithm based on Cholesky decomposition and Lanczos technique,» International Journal of Mathematical and Computer Sciences, pp. 230-233, 2009.
- Loh Yee.KOON , «Implementation of hand vein biometricauthentification on FPGA-BASED embedded systèm,» thesis to obtain the degree of Bachelor of Engineering (Microelectronics), Faculty of Electrical Engineering, Universiti Teknologi Malaysia,, 2010.
- Mohit Sony ,SSandesh Gupta,M.S.Rao and Phalguni GUPTA, «A new vein pattern-based verification system,» International Journal of Computer Science and Information Security, vol. 8, n° %11, pp. 58-63, 2010.
- M.RAJALAKSHMIi and R.RENGARAJ, «Bimetric authentification using near infrared images of palms dorsal vein patterns,» International Journal of Advanced Engineering Technology , vol. 2, n° %14, pp. 384-389, October-December, 2011.
- R.KAVITHA and Little FLOWER, «Localization of palm dorsal vein pattern using image processing for automated intra venous drug needle insertion’’, International Journal of Engineering Science and Technology,» International Journal of Engineering Science and Technology, vol. 3, n° %16, pp. 4833-4838, June 2011.
- M.M.PAL and W. R.JASUTKAR, «Implementation of hand vein structure authentification based system,» BIOINFO Computer Engineering, vol. 2, n° %11, pp. 19-21, 2012.
- C. NANDINIi,C.ASHWINI, Medha APARNA, Nivedita RAMANI, Pragnya KINI and K.ShEEBA , «Biometric authentication by dorsal hand vein pattern,» International Journal of Engineering and Technology, vol.2, n° %15, pp. 837-840, 2012.
- V. a. S.O.RAJANKAR, «Dorsal Hand Vein Biometry by Independent Component Analysis,» International Journal on Computer Science and Engineering, vol. 4, n° %17, pp. 1338-1344, July 2012
- G.SATHISH, S.V. SARAVANAN, S. NARMADHA and S. Uma MAHESWARI, «Personal Authentication System using Hand Vein Biometric,» Int.J.Computer Technology & Applications, vol. 3, n° %11, pp. 383-391, JAN-FEB 2012.
- C. NANDINIi,C.ASHWINI, Medha APARNA, Nivedita RAMANI, Pragnya KINI and K.ShEEBA , «Biometric authentication by dorsal hand vein pattern,» International Journal of Engineering and Technology, vol. 2, n° %15, pp. 837-840, 2012.
- X. H. a. S.-l. M. Yu ZHANG, «Feature Extraction of Hand-Vein Patterns Based on Ridgelet Transform and Local Interconnection Structure Neural Network,» Intelligent Computing in Signal Processing and Pattern Recognition, pp. 870-875, 2006.
- Olivier MOFFETTE, «Extraction des informations nutritionnelles d’une étiquette alimentaire par vision artificielle,» Mémoire de maîtrise électronique, École de technologie supérieure,MONTRÉAL., 2011
- WATANABE, Masaki, ENDOH, Toshio, SHIOHARA, Morito, et al. Palm vein authentication technology and its applications. In : Proc. Biometric Consortium Conference, Arlington VA, USA. 2005.
- M.M.PAL and W. R.JASUTKAR, «Implementation of hand vein structure authentification based system,» BIOINFO Computer Engineering, vol. 2, n° %11, pp. 19-21, 2012.
- M.Madheswaran, M.Deepamalar and, «An improved multimodal palm vein recognition,» International Journal of Computer Theory and Engineering, vol. 2, n° %13, pp. 1793-8201, June, 2010.
- Kar-Ann TOH, How-Lung ENG, Yuen-Siong CHOO,Yoon-Leon CHA, Wei-Yun YAU, and Kay-Soon LOW, «Identity verification through palm vein and crease texture,» chez Advances in Biometrics, Springer-Verlag, Berlin, Heidelberg, Zhang , D. and A.K. Jain , 2005, p. 546–553.
- Y Yi-Bo ZHANG, Qin LI, Jane YOU, and Prabir BHATTACHARYA, «Palm vein extraction and matching for personal authentication,» VISUAL’07 Proceedings of the 9th international conference on Advances in visual information systems, p. 154–164, 2007.
- K.MILKOLAJCZK,C. SCHMID, «A performance evaluation of local descriptors,» IEEE Transactions on Pattern Analysis and Machine Intelligence, vol. 27, n° %110, p. 1615–1630, 2005.
- A.VENCKAUSKAS,N.MORKEVICIUS and . Kulikauskas, «Stydy of finger vein authentification algorithms for physical access control,» Electronics and Electrical Engineering. – Kaunas: Technologija, vol. 121, n° %15, pp. 101-104, 2012.
- Dana LORDROVA, Radim DVORAK, Martin DRAHANSKY, and Filip ORSAG, «A new approach for veins detection,» chez Proceedings of Internation Conference BSBT 2009, Berlin, DE, 2009, pp. 76-80.
- David MULYONO, Horng Shi JINN, «A study of finger Vein biometric for personal identification,» Comput. Sci. & Inf. Eng, November 5, 2008.
- Hyeon Chang LEE, Byung Jun KANG, Eui Chul LEE, Kang Ryoung PARK, «Finger vein recognition using weighted local binary pattern,» Journal of Zhejiang University-SCIENCE C (Computers & Electronics), pp. 514-524, 2010.
- WANG, Yunxin, WANG, Dayong, LIU, Tiegen, et al. Local SIFT analysis for hand vein pattern verification. In : International Conference on Optical Instrumentation and Technology. International Society for Optics and Photonics, 2009. p. 751204-751204-8.
- Benziane, Sarâh et Benyettou, Abdelkader. State of Art: Hand Biometric. International Journal, 1963, vol. 2.
- Debyo.Saptono, «Conception d’un outil de prototypage rapide sur le FPGA,» thèse de doctorat, Universite De Bourgogne, 2011.

This work is licensed under a Creative Commons Attribution 4.0 International License.