Implementing Power Saving Strategies in Wireless Sensor Networks Using IEEE 802.16e
Introduction
In mobile networking, the power consumption of an MS is an important index for measuring portable mobile devices performance because of mobility of MS, which is generally energized by battery, implies that Power-Saving ? Mechanism (PSM) becomes an issue in designing the Medium Access Control (MAC). To enhance the power efficiency of BWA devices based on battery energy, IEEE 802.16e employs the sleep mode operation to minimize MS power usage due to little power consumption in sleep mode. Therefore, power-saving strategy is recently specified in the MAC protocol. Nevertheless, if the MS works in high load, frequent startups will cost so much energy that such an energy-saving mechanism is not energy efficient. And excessive listen window will still consume energy so large limited energy that cannot meet the requirement of practical services when the mobile station works in light traffic load. The model currently implemented is based on the IEEE 802.16 standard (802.16-2004) and the mobility extension 80216e-2005. There are some available features provided by IEEE 802.16 listed below: WirelessMAN-OFDM physical layer with configurable modulation, Time Division Duplexing (TDD), Management messages to execute network entry (without authentication), Default scheduler providing round robin uplink allocation to registered Mobile Stations (MSs) according to bandwidth requested, IEEE 802.16e extensions to support scanning and handovers, Fragmentation and reassembly of Frames.
A typical wireless sensor network consists of sensors powered by small batteries that are difficult to replace if not impossible. Hence, the sensor nodes can only transmit a finite number of bits before they run out of energy. Thus, reducing the energy consumption per bit for end-to-end data transmission is an important design consideration for such networks. We assume that each information bit collected by a sensor is useful for a finite amount of time; after this time the information may become irrelevant. Hence all the bits collected by the sensors need to be communicated to a hub node before a certain deadline. Therefore, the maximum end-to-end transmission delay for each bit must be controlled to meet a given deadline under the hard energy constraint. Since all layers of the protocol stack affect the energy consumption and delay for the end-to-end transmission of each bit.
Packet CS
The CS layer resides on top of the MAC layer and performs the following functions:
- Receives higher-layer PDUs
- Perform classification
- Deliver the CS PDUs to the MAC SA
- Receives CS PDUs from the peer entity
In the current implementation, the Packet CS only performs classification. The method used to classify packets is implementation dependent. It may also be useful to implement multiple solutions in order to find the appropriate connection. The model supports user-defined classifiers such as SDUClassifier & DestClassifier. It uses thedestination IP address to classify the packets.
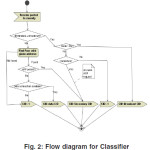
As show in Figure 2, the Classifier uses the destination MAC address located in the packet (and computed at the routing level) and the packet type to determine the proper CID. If there is no match, it will return -1.
MAC sublayer
This section presents the MAC sublayer that currently supports PMP.
MAC module structure
The Mac802_16 is a subclass of the Mac class. It is an abstract class that contains the common elements of the BS and MS. For example it stores the MAC MIB and PHY MIB. It is the interface with other layers for sending and receiving packets. A MAC has a list of packet classifiers (SDUClassifier) that maps each outgoing packet with the proper connection identifier (CID). The current implementation uses the destination IP address as the classifying element.
The ServiceFlowHandler is responsible for handling flow requests/responses. It also stores the list of flows for the node. A SS is registered to a BS, and a BS can be connected to multiple SSs. The class PeerNode contains information about the peer, such as its connections and status. The Connections are also accessed via the connection manager, which contains the list of incoming and outgoing connections.
The Wimax Scheduler abstract class is used to create an interface with the MAC. There are mainly two types of schedulers: one for the BS, and one for the SS. Finally, the MAC computes statistics via StatWatch and ThroughputWatch objects for packet and traffic information. The values are used to trigger events, but can also be printed during the simulation for post processing. Since a BS and an SS have different state machines we defined 2 subclasses, namely Mac802_16BS and Mac802_16SS.
Addressing and connection
Each MAC has a unique address coded as an int that is defined in the MAC class. The model also defines connection identifiers as int but they are carried as 16-bit in the messages. The CIDs are assigned during initialization and dynamic setup of connections. The following connections are created during initialization at the BS:
- Initial Ranging (incoming and outgoing)
- Padding (incoming and outgoing)
- Broadcast (outgoing)
- Adaptive Antenna System (AAS) (outgoing, not used)
The following connections are created during initialization at the SS:
- Initial Ranging (incoming and outgoing)
- Padding (incoming and outgoing)
- Broadcast (incoming)
Additionally, during network entry the following connections are setup and CIDs assigned:
- Basic CID (incoming and outgoing)
- Primary CID (incoming and outgoing)
- Secondary CID (incoming and outgoing)
- Data CIDs. Currently the model only supports one data connection.
MAC PDU format
The model defines a new header for carrying IEEE 802.16 packets. The header contains 3 main elements:
- A virtual physical header is used to carry physical information such as frequency, modulation and cyclic prefix.
- A generic MAC header containing the generic MAC information. The structure can be cast when the packet is a bandwidth request.
- Structures to store the different sub headers. The structures are present in all the packets but the type attribute of the generic header indicates if the entry is valid or not.
When ARQ is enabled, the header also contains feedback information.
Construction and transmission of MAC PDUs
The construction and transmission of packets can be divided into three steps:
Reception of outgoing packet from the upper layer
The MAC runs through the classifiers to find the proper CID. If a valid CID is found, it appends a default MAC header and puts the packet in the connection queue.
Scheduling
Every frame the schedulers go through the list of connections to find the packets to transmit. At the BS, the scheduler performs burst allocation then transfer packets from the connection queue to the bursts. At the MS, it uses the received UL MAP to find the allocation and transfer the packets to the bursts.
Different types of nodes require different packet schedulers. In IEEE 802.16, the BS controls the bandwidth allocation and there are an infinite number of implementations. The model includes an abstract class, WimaxScheduler, created to easily use different packet schedulers. This class already contains two implementations, a scheduler for SSs and a PBS scheduler for BSs.
Schedulers
When implementing a new scheduler, the following four methods must be implemented such as: for initialize the scheduler, to process packets received by the scheduler (such as synchronization messages), start_ulsubframe at the beginning of a new uplink subframe, start_dlsubframe at the beginning of a new downlink subframe.
Transmission
Two timers are going through the DL and UL MAP to transmit the packets stored in the burst queues.
Fragmentation
Fragmentation can be enabled/disabled on a connection based. Currently the default value is to enable the fragmentation. When scheduling packets for transmission, the scheduler checks if fragmentation is enabled for the connection and splits the packet to fit into the burst. The fragmentation context is stored in the Connection. The method transfert_packets in the file scheduling/ wimaxscheduler.cc takes care of transferring packet from their connection queue to the bursts.
Scheduling services
The class structure allows for specifying different data services namely UGS, rtPS, nrTPS, and Best Effort. The services are specified in the ServiceFlow class. The scheduling of the packetsis done by a Scheduler. This scheduler is interacting with the MAC via well defined API allowing custom implementations.
Bandwidth allocation and request mechanisms
This section describes the implementation of the different mechanisms by which a SS can request bandwidth.
Contention resolution
The BS allocates slots that are subject to collisions in the uplink direction. These slots are used in two cases:
- Initial Ranging request
- Bandwidth request
The model supports a truncated binary exponential backoff for contention resolution. The UCD messages broadcasted by the BS contain the window sizes (as a power-of-two value). The BS also decides on the number of slots allocated in each frame. An uplink subframe contains a BwContentionslot and a RngContentionSlot. Bothare subclasses of ContentionSlot which provides the basic mechanisms related to contention. During Network Entry, the SS performs ranging to adjust its transmission power. During this step, the SS generates a RangingRequest. The SS picks a random backoff within the windows provided by the BS and stores it. Then the SS decrements the counter every time a new contention slot is found in the frame. When the counter reaches 0, the packet is being transmitted.
MAC support of PHY
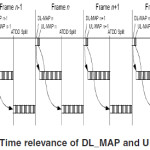
The model currently supports TDD. In this mode, uplink transmission occurs after downlink in each frame. The DL_MAP and UL_MAP messages sent every frame defines the burst allocation and transmission opportunities for each station. The information contained in the UL_MAP belongs to the same frame as shown in Figure 5.
Network entry and initialization
When an MS wants to join a network it needs to perform network entry. As shown in Figure 6 the model implements the following components of the network entry:
- Scan downlink channel
- Obtain transmit parameters
- Initial ranging
- Registration
The following parameters can be configured:
- Timers to perform channel scanning
- Frequency of the DCD/UCD messages
- Parameters for initial ranging (backoff window size and number of slots per frame)
- Channel allocation
Some aspects are IEEE 802.16e are implemented therefore network entry can be reduced if the MS has acquired the transmission parameters from the serving BS or during scanning.
Ranging
Ranging is a mechanism to allow a SS to maintain a good link quality by adjusting itstransmission power and modulation. During the initial ranging, the SS includes the default DIUC profile to use for transmission. This allows the simulation of nodes transmitting at different rates. Currently there is no algorithm implemented to make use of the ranging capabilities. It is used to add additional latency to the network entry. Periodic ranging and CDMA request are also not implemented.
QoS
The framework defines structures to support the implementation of schedulers that make use of the different classes of service . Each Connection can be associated with a ServiceFlow and corresponding QoS parameters. QoS flows are not currently implemented in this model. By default, one data connection in each direction is setup during the network entry and the BE is used for allocation.
MAC layer handover procedures
The model supports layer 2 mobility. Depending on the configuration, the MS may perform scanning and handover between BSs. This section presents the configuration parameters that affect the handover capability.
Scanning
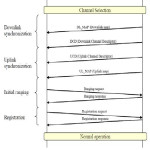
When the link quality deteriorates, the MS can send a MOB-SCN_REQ to the serving BS to request scanning interval for the purpose of finding surrounding BSs. Figure 8 shows the messages sequence during scanning as implemented in the model.
Figure 8: Scanning procedure
To trigger the sending of a MOB-SCN_REQ, the MS monitors the signal level of the incoming packets. When the level crosses a threshold, the message is sent. By default, the threshold is set to the RXThreshold therefore scanning is not used. To enable scanning, change the attribute of the MIB to a value greater than 1.0. The higher the value, the sooner the scanning will trigger. During scanning, the MS collects RSSI values of incoming packets. These values are reported to the serving BS that uses the information to select the best target BS.
After the MS receives indication of the selected BS, it waits for a few frames before indicating its intention to perform handover. The introduction of the delay is to allow the traffic buffered during scanning to be exchanged before switching BSs. Different scanning modes are implemented:
- In scan without association, the MS attempts to identify and synchronize with one or more BSs. It also estimates the signal quality.
- In association level 0, the target BS has no information about the scanning MS and only provides contention-based ranging allocations. After sending a ranging request, the MS waits for a response from the BS with a default timeout value of 50ms.
- In association level 1, the serving BS negotiates with the target BSs a time at which the MS will find a dedicated ranging region. After sending a ranging request, the MS waits for a response from the BS with a default timeout value of 50ms.
To allow these different scanning modes and to perform fast handovers, the WiMAXCtrlAgent is required. The WiMAXCtrlAgent is an Agent performing 3 functions. The first one is to exchange DCD/UCD information between the neighbor BSs. The second is to trigger the sending of NBRADV messages to the MSs. The third one is to synchronize the serving BS and the target BSs when performing scanning level 1 or 2. The messages are exchanged over wired links using standard IP packets.
OFDM PHY
OFDM physical layer
The OFDM physical layer is used to transmit packets in the implemented model. The configuration is done for the frequency bandwidth and cyclic prefix. Since it inherits from the WirelessPhy class, attributes such as frequency or transmission power can also be configured. As Shown in Figure 17, the physical layer can be in different states. When in sending mode, all incoming packets are discarded. In receiving mode, packets cannot be sent. Furthermore, the packet header contains virtual information, such as frequency, modulation, and cyclic prefix, which are used to filter incoming packets.
The model supports different modulations. The MAC layer allocates bursts that can use different modulations according to distance or interference. This affects the data rate and transmission time. The physical layer includes helper functions called by the MAC layers when transmitting data:
- getTrxTime returns the time required to senda packet given its size and modulation.
- getMaxPktSize is the reverse function andreturns the maximum packet size given the number of OFDM symbols available and the modulation used.
The node_on and node_off functions enable or disable blocking all transmissions and receptions of packets, but is not currently linked to any power consumption mechanisms.
OFDM Packet schedulers
Scheduler
The scheduler implements a Best-Effort scheduler coupled with a Round Robin algorithm to distribute the bandwidth allocations among the users. To support BE, bandwidth requests are generated at the SS indicating the amount of data to transfer. The scheduler also allows users to have different modulations.
sets the modulation to use for the initial ranging and bandwidth requests slots.
Scheduler
Creates a packet scheduler for SS. Profile bursts are created by default as follows
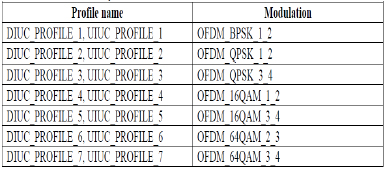
By default, the profile (modulation) is the same for BOTH downlink and uplink for communication between a SS and a BS. Set the cyclic prefix to use. Valid values are 0.25 (1/4), 0.125 (1/8), 0.0625 (1/16), 0.03125 (1/32) By increasing the cyclic prefix, the overhead is increasing thus reducing the maximum through put.
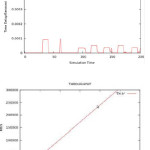
Simulation Result
After implementation of modulation techniques, it is found that packet loss is reduced by increasing the throughput with reducing time & by decreasing delay with increasing time.
Future Work
By analyzing the behavior of a mobile station with modulation techniques such as BPSK, QPSK, & 16 QAM, it is found that packet loss is reduced by increasing the throughput with reducing time & by decreasing delay with increasing time. Packing, Association level 2 of scanning, & QoS flows will be implemented in next model. OFDMA (Orthogonal Frequency Division Multiple Access) PHY (Physical Layer) will be considered. Energy consumption and mean delay of power saving mechanism based on cross-layer design, a heuristic algorithm will be implemented to adapt the parameters of sleep-mode mechanism to the mobile station traffic and the mean delay requirement.
Conclusion
In this paper, we introduced the power-saving mechanism of the IEEE 802.16e based on modulation techniques. Power saving strategies based on modulation techniques design, which tunes the initial sleep window dynamically according to the flow intervals information from the traffic load of the BS physical layer, was proposed to enhance performance of the power consumption and bounds the delay in the required range. Extensive simulation results show that the proposed algorithm can improve the power consumption significantly. Implementing modulation technique it found that packet loss is reduced by increasing the throughput with decreasing time & by decreasing delay with increasing time. Some aspects of IEEE 802.16e are implemented therefore network entry can be reduced if the MS has acquired the transmission parameters from the serving BS or during scanning.
References
- IEEE802.16e-2006, IEEE Standard for Local and metropolitan area networks, Part 16: Air Interface for Broadband Wireless Access System MS C Amendment for Physical and Medium Access Control Layers for Combined Fixed and Mobile Operation in Licensed Bands, (2006).
- IEEE802.16-2004, IEEE Standard for Local and metropolitan area networks, Part 16: Air Interface for Fixed Broadband Wireless Access Systems (2004).
- I. F. Akyildiz, W. Su, Y. Sankarasubramaniam, and E. Cayirci. Wireless sensor networks: a survey. Computer Networks, 38(4):393-422 (2002).
- G. Bianchi. IEEE 802.11-saturation throughput analysis. IEEE Communications Letters, 2(12): 318-320 (1998).
- C. F. Chiasserini and M. Garetto. An analytical model for wireless sensor networks with sleeping nodes. Mobile Computing, IEEE Transactions on, 5: 1706-1718 (2006).
- T. V. Dam and K. Langendoen. An adaptive energy-efficient MAC protocol for wireless sensor networks. In Proceedings of the First international conference on Embedded networked sensor systems, pages 171–180, New York, USA, 2003.K. K. II, and P. Mohapatra. Medium access control in wireless sensor networks. Computer Networks,51(4): 961-994 (2007).
- C. Y. Lin, W. C. Peng, Y. C. Tseng, Efficient In-Network Moving Object Tracking in Wireless Sensor Networks, IEEE Trans. on Mobile Computing, 5(8): (2006).
- W. Ye, J. Heidemann, D. Estrin, An Energy-Efficient MAC Protocol for Wireless Sensor Networks, in: Proc. of the 21st IEEE Infocom, 1567-1576 (2002.
- Vincent S. Tseng, Kawuu W. Lin, Ming-Hua Hsieh, Energy Efficient Object Tracking in Sensor Networks by Mining Temporal Moving Pattern, in: IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC’08), 2008
- Y. Xu, J. Winter, W.C. Lee, Prediction-Based Strategies for Energy Saving in Object Tracking Sensor Networks, in: Proc. of the 5th IEEE Int’l Conf. on Mobile Data Management (MDM’04), 2004, pp. 346-357.
- T. Shepard, “A channel Access Scheme for Large Dense Packet Radio Networks”, in Proc of ACM SIGCOMM 1996, pp. 219-230, 1996
- Vibhakar pathak, Dr. Krishna Chandra Roy and Santosh Kumar Singh, “cross layer aware adaptive mac based on knowledge based reasoning for cognitive radio computer networks”, International Journal of Next Generation Networks (IJNGN) Vol.2, No.2, June 2010.
- Y. Awad, L. H. Crockett and R. W. Stewart, “OFDM TRANSCEIVER FOR IEEE 802.20 STANDARDS”,
- Shuguang Cui and Andrea J. Goldsmith,” Cross-layer Optimization in Sensor Networks with Energy Constraints”.
- A. J. Goldsmith and S. B. Wicker, “Design challenges for energy constrained Ad Hoc wireless networks,” IEEE Wireless Communications Magazine, 8-27 (2002).
- R. Madan, S. Cui, S. Lall, and A. J. Goldsmith, “Cross-layer design for lifetime maximization in interference-limited wireless sensor networks,” to appear at IEEE Infocom’05, Florida (2005).
- S. Cui, A. J. Goldsmith, and A. Bahai, “ Energy-efficiency of MIMO and Cooperative MIMO in Sensor Networks,” at IEEE Journal on Selected Areas of Communications, 22(6) (2004).
- J. Xiao, S. Cui, Z. Q. Luo, and A. J. Goldsmith, “Joint Estimation in Sensor Networks under Energy Constraint,” at Proceedings of IEEE first conference on Sensor and Ad Hoc Communications and Networks, Santa Clara, CA, October, 2004.
- S. Cui, J. Xiao, A. J. Goldsmith, Z. Q. Luo, and H. V. Poor, “Energy-Efficient Joint Estimation in Sensor Networks: Analog vs. Digital,” to appear at IEEE ICASSP, Philadelphia, PA, (2005).

This work is licensed under a Creative Commons Attribution 4.0 International License.