Anisha Kumar
Department of Studies in Computer science, Pooja Bhagavat Memorial Mahajan PG Centre, Department of Computer Science, Mysore - 570 017 (India).
Article Publishing History
Article Received on :
Article Accepted on :
Article Published :
Article Metrics
ABSTRACT:
Information Technology solutions have paved a way to a new world of internet, business networking and e-banking, budding as a solution to reduce costs, change the sophisticated economic affairs to more easier, speedy, efficient, and time saving method of transactions. Internet has emerged as a blessing for the present pace of life but at the same time also resulted in various threats to the consumers and other institutions which results in committing cyber crime. Despite the increase in government compliance requirements and the proliferation of security tools, companies continue to underestimate the threat from phishing, data loss, and other cyber vulnerabilities. This paper contributes an understanding of the effects of negative use of Information technology, as how a simple technological aspect of file deletion can result in cyber crime. A few aspects to trace the deleted information with restoring software is also mentioned in this paper.
KEYWORDS:
File deletion; Restoring; Cyber crime; Internet
Copy the following to cite this article:
Kumar A. A Concept of File Deletion and Restoration as A Threat to Commit Cyber Crime. Orient. J. Comp. Sci. and Technol;4(1)
|
Copy the following to cite this URL:
Kumar A. A Concept of File Deletion and Restoration as A Threat to Commit Cyber Crime. Orient. J. Comp. Sci. and Technol;4(1). Available from: http://www.computerscijournal.org/?p=2394
|
Introduction
Cyber crime consist of any criminal act dealing with computers and networks called as hacking. Additionally, cyber crime also includes traditional crimes conducted through the Internet like telemarketing and Internet fraud, identity theft, and credit card account thefts, as these illegal activities are committed through the use of a computer and the Internet [1]. The first recorded cyber crime took place in the year 1820.That is not surprising considering the fact that the abacus, which is thought to be the earliest form of a computer, has been around since 3500 B.C. in India, Japan and China. The era of modern computers, however, began with the analytical engine of Charles Babbage. In 1820, Joseph-Marie Jacquard, a textile manufacturer in France, produced the loom. This device allowed the repetition of a series of steps in the weaving of special fabrics. This resulted in a fear amongst Jacquard’s employees that their traditional employment and livelihood were beingthreatened. They committed acts of sabotage to discourage Jacquard from further use of the new technology. This is the first recorded cyber crime [2].
In the field of computer security, phishing is the criminally fraudulent process. It is a form of Internet fraud that involves tricking people into revealing confidential information like credit card details, user names and passwords by means of a fake e-mail that appears to come from a well-known, legitimate organization like a bank or any institution heads .This paper gives a brief description on the concept of file deletion and restoration in windows which is an aid to lead to the phishing activity as a result of threat to commit a cyber crime.
File allocation techniques
File allocation is done using different allocation methods such as contiguous allocation, linked allocation and indexed allocations depending on the disk partitions and mounting resulting in diskspace. Each partition can either be “raw” containing no file system or “cooked” containing a file system. Raw disk is used as swap space, as it uses its own format on disk and not any file system[3]. It is also used for database purpose to format the data to suit some needs.
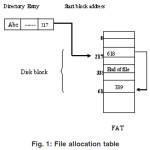
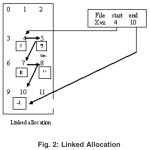
In general the process of file allocation using links helps for a better understanding about the concept of file deletion. With a linked allocation (see fig (i)), each file is a linked list of disk blocks, the disk blocks may be scattered anywhere on the disk. The File allocation table consist of link details as pointers to the starting address of a particular file (see fig (ii)).
Since disk space is limited, we need to reuse the space from deleted files for new files. To keep track of free disk space the system maintains a free space list which records all free disk blocks those not allocated to some file or directory. When a file is deleted its disk space is also added to the free space list.
File deletion basic concepts
When a file is deleted from the computer, its contents are not immediately destroyed. Windows simply marks the hard drive space as being available for use by changing one character in the file table so that the file entry won’t be displayed. That is an operating system first marks the space on the hard drive that the file occupied as a free space. Since the link is lost and the space is free to be overwritten by new data on top of the existing deleted contents, at this point file recovery process becomes a lot more difficult. Hence if a little computing is done the chance of retrieving the deleted file using restoration tools are high.
There are some other serious issues that could avoid the restoration as the hard drive is overwritten in cases where it is pretty full , the odds are much greater that Windows will grab your precious unallocated space for its next write. Or, if you defrag the hard drive, you run the risk of unused parts of the drive being overwritten. But these issues occur very rarely in personal computers so its always better to be safe from keeping our id’s or information secure by simply starting up Windows or, to a lesser extent, shutting down Windows which causes many tiny files to be written as the computation increases and restoration becomes difficult.
Restoration is a freeware program that restores deleted files no longer in the Recycle Bin and from disk space. There are many restoration software available like FileRestorePlus[2] which is a quick and effective way to restore accidentally deleted files. It can also recover files that have been emptied from the Recycle Bin, permanently delete files within Windows using the Shift + Delete, and files that have been deleted from within a Command Prompt.
Recovery software created to recover detail when a mobile phone software crashes or to recover details from a disk is similar to the basic common c source code given below for the restoration software work that was carried out in torus solutions.[4]
Finding
Program created for restoration
The list of header files included in the source programme created as a restoration software for the cause mentioned above is given below [4]
#include <ctype.h> // character type for upper and
lowercase etc.
18 #include <errno.h>
19 #include <fcntl.h>// file control option header file
for the purpose of setting flags etc.
20 #include <getopt.h>
21 #include <limits.h>
22 #include <linux/input.h>
23 #include <stdio.h>
24 #include <stdlib.h>
25 #include <sys/reboot.h>
26 #include <sys/types.h>
27 #include <time.h>
28 #include <unistd.h>
29
40 static const struct option OPTIONS[] = {
41 { “send_intent”, required_argument, NULL, ‘s’ },
42 { “update_package”, required_argument, NULL,
‘u’ },
43 { “wipe_data”, no_argument, NULL, ‘w’ },
44 { “wipe_cache”, no_argument, NULL, ‘c’ },
45 };
46
47 static const char *COMMAND_FILE =
“CACHE:recovery/command”;
48 static const char *INTENT_FILE =
“CACHE:recovery/intent”;
49 static const char *LOG_FILE =
“CACHE:recovery/log”;
50 static const char *SDCARD_PACKAGE_FILE =
“SDCARD:update.zip”;
51 static const char *TEMPORARY_LOG_FILE =
“/tmp/recovery.log”;
52
53 /*
54 * The recovery tool communicates with the main
system through /cache files.
55 * /cache/recovery/command – INPUT – command
line for tool, one arg per line
56 * /cache/recovery/log – OUTPUT – combined log
file from recovery run(s)
57 * /cache/recovery/intent – OUTPUT – intent that
was passed in
58 *
59 * The arguments which may be supplied in the
recovery.command file:
60 * —send_intent=anystring – write the text out to
recovery.intent
61 * —update_package=root:path – verify install an
OTA package file
62 * —wipe_data – erase user data (and cache),
then reboot
63 * —wipe_cache – wipe cache (but not user data),
then reboot
64 *
65 * After completing, we remove /cache/recovery/
command and reboot.
66 */
67
68 static const int MAX_ARG_LENGTH = 4096;
69 static const int MAX_ARGS = 100;
70
71 // open a file given in root:path format, mounting
partitions as necessary
72 static FILE*
73 fopen_root_path(const char *root_path, const
char *mode) {
74 if (ensure_root_path_mounted(root_path) != 0)
{
75 LOGE(“Can’t mount %s\n”, root_path);
76 return NULL;
77 }
78
79 char path[PATH_MAX] = “”;
80 if (translate_root_path(root_path, path,
sizeof(path)) == NULL) {
81 LOGE(“Bad path %s\n”, root_path);
82 return NULL;
83 }
84
85 // When writing, try to create the containing
directory, if necessary.
86 // Use generous permissions, the system (init.rc)
will reset them.
87 if (strchr(“wa”, mode[0]))
dirCreateHierarchy(path, 0777, NULL, 1);
8889 FILE *fp = fopen(path, mode);
90 if (fp == NULL) LOGE(“Can’t open %s\n”, path);
91 return fp;
92 }
93
94 // close a file, log an error if the error indicator is
set
95 static void
96 check_and_fclose(FILE *fp, const char *name)
{
97 fflush(fp);
98 if (ferror(fp)) LOGE(“Error in %s\n(%s)\n”, name,
strerror(errno));
99 fclose(fp);
100 }
101
102 // command line args come from, in decreasing
precedence:
103 // – the actual command line
104 // – the bootloader control block (one per line,
after “recovery”)
105 // – the contents of COMMAND_FILE (one per
line)
106 static void
107 get_args(int *argc, char ***argv) {
108 if (*argc > 1) return; // actual command line
arguments take priority
109 char *argv0 = (*argv)[0];
110
111 struct bootloader_message boot;
112 if (!get_bootloader_message(&boot)) {
113 if (boot.command[0] != 0 && boot.command[0]!= 255) {
114 LOGI(“Boot command: %.*s\n”,
sizeof(boot.command), boot.command);
115 }
116
117 if (boot.status[0] != 0 && boot.status[0] != 255)
{
118 LOGI(“Boot status: %.*s\n”, sizeof(boot.status),
boot.status);
119 }
120
121 // Ensure that from here on, a reboot goes back
into recovery
122 strcpy(boot.command, “boot-recovery”);
123 set_bootloader_message(&boot);
124
125 boot.recovery[sizeof(boot.recovery) – 1] = ‘\0’;
// Ensure termination
126 const char *arg = strtok(boot.recovery, “\n”);
127 if (arg != NULL && !strcmp(arg, “recovery”)) {
* MAX_ARGS);//
145 (*argv)[0] = argv0; // use the same program
name
146
147 char buf[MAX_ARG_LENGTH];
148 for (*argc = 1; *argc < MAX_ARGS && fgets(buf,
sizeof(buf), fp); ++*argc) {
149 (*argv)[*argc] = strdup(strtok(buf, “\r\n”)); // Strip
newline.
150 }
151
152 check_and_fclose(fp, COMMAND_FILE);
153 LOGI(“Got arguments from %s\n”,
COMMAND_FILE);
154 }
155
156
157 // clear the recovery command and prepare to
boot a (hopefully working) system,
158 // copy our log file to cache as well (for the
system to read), and
159 // record any intent we were asked to
communicate back to the system.
160 // this function is idempotent: call it as many
times as you like.
161 static void
162 finish_recovery(const char *send_intent)
163 {
164 // By this point, we’re ready to return to the
main system…
165 if (send_intent != NULL) {
166 FILE *fp = fopen_root_path(INTENT_FILE,
“w”);
167 if (fp != NULL) {
168 fputs(send_intent, fp);
169 check_and_fclose(fp, INTENT_FILE);
170 }
171 }
172
173 // Copy logs to cache so the system can find
out what happened.
174 FILE *log = fopen_root_path(LOG_FILE, “a”);
175 if (log != NULL) {
176 FILE *tmplog =
fopen(TEMPORARY_LOG_FILE, “r”);
177 if (tmplog == NULL) {
178 LOGE(“Can’t open %s\n”,
TEMPORARY_LOG_FILE);179 } else {
180 static long tmplog_offset = 0;
181 fseek(tmplog, tmplog_offset, SEEK_SET); //
Since last write
182 char buf[4096];
183 while (fgets(buf, sizeof(buf), tmplog)) fputs(buf,
log);
184 tmplog_offset = ftell(tmplog);
185 check_and_fclose(tmplog,
TEMPORARY_LOG_FILE);
186 }
187 check_and_fclose(log, LOG_FILE);
188 }
189
190 // Reset the bootloader message to revert to a
normal main system boot.
191 struct bootloader_message boot;
192 memset(&boot, 0, sizeof(boot));
193 set_bootloader_message(&boot);
194
195 // Remove the command file, so recovery won’t
repeat indefinitely.
196 char path[PATH_MAX] = “”;
197 if
(ensure_root_path_mounted(COMMAND_FILE) !=
0 ||
198 translate_root_path(COMMAND_FILE, path,
sizeof(path)) == NULL ||
199 (unlink(path) && errno != ENOENT)) {
200 LOGW(“Can’t unlink %s\n”, COMMAND_FILE);
201 }
202
203 sync(); // For good measure.
204 }
251 if (key == KEY_DREAM_BACK &&
ui_key_pressed(KEY_DREAM_HOME)) {
252 // Wait for the keys to be released, to avoid
triggering
253 // special boot modes (like coming back into
recovery!).
254 while (ui_key_pressed(KEY_DREAM_BACK) ||
255 ui_key_pressed(KEY_DREAM_HOME)) {
256 usleep(1000);
257 }
258 break;
259 } else if (alt && key == KEY_W) {
260 ui_print(“\n”);
261 erase_root(“DATA:”);
262 erase_root(“CACHE:”);
263 ui_print(“Data wipe complete.\n”);
264 if (!ui_text_visible()) break;
265 } else if (alt && key == KEY_S) {
266 ui_print(“\nInstalling from sdcard…\n”);
267 int status =
install_package(SDCARD_PACKAGE_FILE);
268 if (status != INSTALL_SUCCESS) {
2 6 9
ui_set_background(BACKGROUND_ICON_ERROR);
270 ui_print(“Installation aborted.\n”);
271 } else if (!ui_text_visible()) {
272 break; // reboot if logs aren’t visible
273 }
274 ui_print(“\nPress Home+Back to reboot\n”);
289
290 // If these fail, there’s not really anywhere to
complain…
291 freopen(TEMPORARY_LOG_FILE, “a”,
stdout); setbuf(stdout, NULL);
292 freopen(TEMPORARY_LOG_FILE, “a”, stderr);
setbuf(stderr, NULL);
293 fprintf(stderr, “Starting recovery on %s”,
ctime(&start));
294
295 ui_init();
345 } else {
346 status = INSTALL_ERROR; // No command
specified
347 }
348
349 if (status != INSTALL_SUCCESS)
ui_set_background(BACKGROUND_ICON_ERROR);
350 if (status != INSTALL_SUCCESS ||
ui_text_visible()) prompt_and_wait();
351
352 // If there is a radio image pending, reboot now
to install it.
353 maybe_install_firmware_update(send_intent);
354
355 // Otherwise, get ready to boot the main
system…
356 finish_recovery(send_intent);
357 ui_print(“Rebooting…\n”);
358 sync();
359 reboot(RB_AUTOBOOT);
360 return EXIT_SUCCESS;
361 }[4]
Conclusion
In this paper the first level work on the concept of file deletion and restoration software is explained which can avoid cyber crime to some extend in personal computers. In the second level of work c programming language and concepts of pointers are used to retrieve the memory address space of deleted information which works like a restoration software. This work was carried out at Torus Solutions, Mysore under the guidance of Mr.Senthil Kumar and the concepts were studied with the help of Dr. P. Vinod.
References
- (Dr) P. Vinod Bhattathiripad Cyber crime investigation consultant Kerala (http://w w w.saintgits.org/main/sie/Computer%20Science/Annual%) 20Report. asp A seminar conducted by Dr Vinod at kerala on 7th August,2009 as given in the annual report of the address mentioned above is the guidelines for basic ground work on cyber crime and file system.
- http://download.cnet.com/Restoration/3000- 2094_4-10322950.html
- OperatingSystem Concepts, 5th Edition, published in 2000 Authors : Silberschatz, Galvin, Gagne Chapters 10,11, pages 343- 355,360-380
- www.torussolution.com a software firm in mysore,Karnataka.

This work is licensed under a Creative Commons Attribution 4.0 International License.