Introduction
In Wireless Sensor Networks (WSNs)¹ nodes are usually operated by batteries and left unattended after deployment. Considering the limited power sources of nodes, such as batteries whose recharge or replacement is difficult or impossible, energy consumption is a vital point, and it occurs in three states: sensing, data processing, and communication. Communication among nodes is the major consumer of energy in compare with sensing and data processing which consists of three modes: idle listening, receiving, and transmitting. In communications among nodes, if the RF transceiver stays in receive mode waiting for possible incoming packets (idle listening), the battery will be exhausted since the power consumption of idle listening is normally not much smaller than transmitting. Many research efforts have focused on developing power saving schemes for WSNs. These schemes include power saving hardware design, power saving topology design, power-efficient Medium Access Control (MAC) layer protocols.
MAC protocol lies in the low layer of the protocol stack², which is crucial to guarantee WSN’s efficient communication, according to the design principle of the traditional layered network protocol stack, MAC protocols is responsible for channel assignment and access control, while forwarding path construction and selection are usually left to up-layer routing protocols. Therefore, most MAC protocols do not have the ability to choose receiving node independently, and it is difficult to achieve load balance. In communication, some nodes die too early due to energy consumption, which limits the network lifetime. The MAC protocols directly control the communication modes in WSNs, likewise control energy consumption, which directly influence the lifetime of the networks. Therefore, there has been recent attention on developing energy efficient MAC protocols in wireless sensor networks. The main idea of MAC protocol for wireless sensor networks is to support a duty cycling mechanism to consume the energy while transmitting or receiving useful data only and not in idle listening mode.
Many MAC protocols for WSNs have been developed. These are broadly classified into two types:
Schedule-Based MAC Protocols
In these types of protocols schedule exists, regulating which participant may use which resource at which time³ (TDMA component) frequency band in a given physical space with a given code CDMA are typical resources.Schedule can be fixed or computed on demand. Usually no issues of collisions, overhearing, idle listening but time synchronization is required.
Examples: TDMA, FDMA, CDMA
Contention-Based MAC Protocols
In these types of protocols randomization is used somehow risk of colliding packets is deliberately taken hoping that coordination overhead can be saved, resulting in overall improved efficiency,mechanisms to handle or to reduce probability or the impact of collisions required .
Examples: ALOHA (pure & slotted), CSMA
Related Work
Let’s look at the some of the MAC protocols that are proposed to enhance energy efficiency, load balance, low latency and high channel utilization and discuss the drawbacks in each of the protocol.
S-MAC
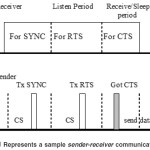
Sensor-MAC4 provides energy efficiency by locally managed synchronizations and periodic sleep listen schedules. Here neighbouring nodes form virtual clusters to set up a common sleep schedule. If two neighbouring nodes reside in two different virtual clusters, they wake up at listen periods of both clusters.
Here schedule exchanges are accomplished by periodical SYNC packet broadcasts to immediate neighbours. The period for each node to send a SYNC packet is called the synchronization period.
Drawbacks
S-MAC algorithm is this possibility of following two different schedules, which results in more energy consumption via idle listening and overhearing.
Periodic sleep may result in high latency especially for multi-hop routing algorithms, since all immediate nodes have their own sleep schedules and this is called sleep delay.
As the sleep and listen periods are predefined and constant it decreases the efficiency of the algorithm under variable traffic load.
T-MAC
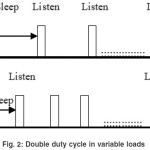
Timeout-MAC (T-MAC)5 is proposed to enhance the poor results of S-MAC protocol under variable traffic load. In T-MAC the listen period ends when no activation event has occurred for a time threshold Th. Variable load in sensor networks are expected, since the nodes that are closer to the sink must relay more traffic.
When a sender node receives this sleep period decrement signal, it checks its queue for packets destined to that receiver node. If there is one, it decides to double its duty cycle when its battery level is above a specified threshold. The duty cycle is doubled so that the schedules of the neighbours will not be affected. The latency observed with T-MAC is better than the one observed with S-MAC.
Drawback
Although T-MAC gives better results under these variable loads, the synchronization of the listen periods within virtual clusters is broken. This is one of the reasons for the early sleeping problem where the node goes to sleep when a neighbor still has messages for it.
D-MAC
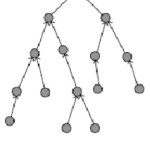
Destination-MAC (D-MAC)6 principal aim is to achieve very low latency, but still to be energy efficient. It could be summarized as an improved Slotted Aloha algorithm where slots are assigned to the sets of nodes based on a data gathering tree as shown in Fig. 3.
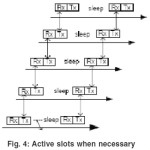
During receive period of a node, all of its child nodes has transmit periods and contend for the medium. Low latency is achieved by assigning subsequent slots to the nodes that are successive in the data transmission path as shown in figure 4, in certain scenarios network latency is crucial but in such aspects D-MAC could be strong candidate.
Drawbacks
The data transmission paths may not be known in advance, which precludes the formation of the data gathering tree. It also lacks the flexibility to support communication other than converge cast.
B-MAC
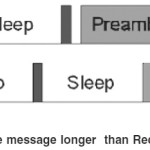
Berkeley MAC7 is a carrier sense media access protocol that provides a flexible interface to obtain ultra low power operation, and high channel utilization. Each node has an independent schedule Here as shown in figure 5 node sends the data packet following with a long preamble that is slightly longer than the sleep period of the receiver. During the active period, a node samples the channel and if a preamble is detected, it remains awake to receive the data. With the long preamble, a sender is assured that at some point during the preamble the receiver will wake up, detect the preamble, and remain awake in order to receive the data. It is low power listening (LPL). The major advantage of LPL is that it minimizes active period when there is no traffic. To achieve low power operation, B-MAC employs an adaptive preamble sampling scheme to reduce duty cycle and minimize idle listening.
Drawback
B-MAC has the overhearing problem because of the long preamble there will be considerable energy usage of sender and increases per-hop latency.
Proposed Protocol
Network Lifetime
The requirements for WSNs may vary depending on the target applications; therefore we need to explore the network lifetime issue to design a more comprehensive solution. The network lifetime8 can be defined as one of the following:
Time To Network Partitioning
Network partitioning means that a network is divided into two or more partitions since the intermediate nodes between these partitions run out of energy. When network partitioning occurs, there would not exist any path between two partitions, and consequently, the network does not work properly.
Time To A Sensing Hole’s Occurrence
A sensing hole means a blind point where the sensor network cannot sense. If every node in charge of an area dies, a sensing hole takes place. Accordingly, any sensing event in that area cannot be delivered to the sink. Thus, time to a sensing hole’s occurrence is equivalent to the network lifetime in the monitoring applications.
Time To First Node’s Death
Some WSN applications might be sensitive to a single node’s exhaustion of energy, possibly due to the sparse deployment of sensor nodes. In such applications, the network would not work as appropriately as expected when even a single node dies. In such cases, time to first node’s death degrades the QoS or incurs the sensing hole problem. In a densely deployed network, this definition can be extended to the time until a certain percentage of the sensor nodes die.
looks forward to overcome the drawbacks of the approaches discussed. Our approach is simple; we assume that network initialization phase each node has provided with its own wake-up scheme and sleep periods depending on network requirements. This may in turn results to idle listening especially in variable traffic load and resulting to low channel utilization and fast degrade in the networks lifetime. Our protocol inherits the strategies of S-MAC .The entire communication process in our approach remains the same as seen in S-MAC [4]. The Only variation in our approach is that the sleep and wake-up slots for nodes, during initialization the allotted time slots will vary accordingly depending on the network traffic and message load. That is when a node is in listen state it starts the timer and records the delay D in the packet it received and accordingly.
Most of the existing MAC protocols for WSNs focus on improving the lifetime of each node without considering load balanced energy consumption among nodes. With these approaches, prolonging the node’s lifetime does not always result in the longer network lifetime. A node suffering more traffic may die far earlier than others, resulting in the early termination of the network, regardless of the remaining energy levels of other nodes. Therefore, it is of great significance to take into account not only the node lifetime but also the entire network lifetime in designing a MAC protocol for WSNs.
Protocol Overview
The proposed protocol Delay Adjust MAC it adjusts its sleep and wake-up slots by adding the delay value with this approach it automatically adjusts to the networks load. The calculation of the delay value and the parameters involved and energy required for the adjustment of network’s slots are discussed in next phase.
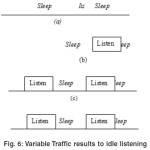
Let us look at the problem of idle listening due to traffic variations in detail with the help of an example, consider nodes with their sleep and wake-up time fixed and assume that network is implementing S-MAC approach.
In accordance to figure 6, co-ordination between figure 6(a) and (b) is the best as each have different slots, the energy saving and perfect channel utilization is seen ,but the co-ordination for
figure 6(c) and (d) has reached to same time slots that will cause high energy consumption and low channel utilization. This worst co-ordination will result to degrade in networks lifetime, and may also result lo low performance of the network.
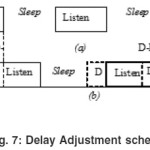
Let us look at the strategy of our proposed approach Delay adjust MAC where the variable adjustment of listen and sleep periods will result to overcome the idle listening and improve energy efficiency.
As shown in the figure 7 the node will determine the delay in received packet at early stage of initialization and in the next time slot it will adjust its sleeping and wake-up scheme as seen at right part figure 7(b), the delay D in first listen slot is calculated and accordingly in time to listen in next slot is delayed simultaneously. The dotted module is actual listen (old) schedule and the high lighted module is the new listen schedule for the corresponding node in network.
Let us look at the algorithmic approach to the delay adjust protocol.
Parameters
Request to send (RTS), Clear to send (CTS), Timer (t), Delay (D), Energy consumed for adjusting (ECA), Energy wasted in idle listening (EWI), Threshold value for delay (Th),Begin Listen (BL), End Listen (EL), Begin Sleep (BS) and End Sleep (ES).
Algorithm Delay Adjust (Bl, El, Bs, Es)
When Node Starts to listen at send signal
RTS
Reset timer t i.e. t←0
Repeat Until CTS is received
Increment timer t i.e. t← t +1
Wait for CTS
Assign Timer value to Delay i.e. D← t
If (D< =Th) then Quit
BL=BL+D
EL=EL+D
BS=BS+D
ES=ES+D
Return values and Quit
Threshold value (Th) for the delay is determined based on EWI and ECA values.ECA value is the energy consumed by the network to adjust the sleep and listen cycles. EWI [9] value can be determined by the time node waits for the receiving CTS signal for the receiver node, base on which a constant value for D is determined and called as threshold.
Energy Consumption (Mj)
Analysis of Protocol
The Algorithm when implemented does not show the expected performance at the initialization phase but it shows very improvement at intermediate phases. This is because the slight variations in Delay and Delay threshold may not occur at early stages of communication between the nodes as the nodes and their communication increases network traffic varies in such cases the performance of the algorithm will be high. This Delay Adjust MAC scheme is very strong when huge traffic variations occur in the network.
The main goal of the experimentation is to look at the energy consumption of each node when utilizing different MAC protocols and under different traffic loads. The source periodically generate a sensing message, divided into some fragments, each fragment as an independent packet and uses RTS/CTS for each of them. We change the traffic load by varying the inter-arrival period of the messages.4 If the message inter-arrival period is 3 seconds, a message is generated every 3 seconds by each source node. In our following experiments, the message inter-arrival period varies from 1s to 10s. For each traffic pattern, we have done 10 independent tests to measure the energy consumption of each node for S-MAC and proposed Delay Adjust MAC protocol. In each test, each source periodically generates 10 messages, which in turn is fragmented into 10 small data packets. For the highest rate with a 1s inter arrival time, the wireless channel is nearly fully utilized due to its low bandwidth. The energy consumption in each node is then calculated by multiplying the time with the required power to operate in terms of milli joules.
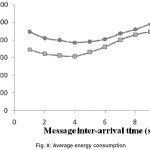
The Experiment includes S-MAC protocol and our proposed protocol, is denoted as DA-MAC. Figure 8 shows the measured average energy consumption for intermediate nodes. The traffic is heavy when the message inter-arrival time is less than 4s. We can see in the light traffic case S-MAC consumes more energy than DA-MAC as idle listening occurrences are more vulnerable and consumes more energy. In heavy traffic case, S-MAC consumes slightly more energy than DA-MAC. One reason is that SMAC has synchronization overhead of sending and receiving SYNC packets. Another reason is that SMAC introduces more latency and actually uses more time to pass the same amount of data. In fact, if the traffic is extremely heavy and a node does not have any chance to follow its sleep schedule, the scheme of periodic listen and sleep does not benefit at all.
The above graph in figure 8 represents the analysis of the proposed DA-MAC with the existing SMAC protocol where the simulations shows that energy consumption compared to S-MAC is varies with the variations of traffic is more and in normal cases the energy consumption remains the same.
Conclusion
In this paper we had presented the challenges of energy consumption in WSN and discussed the various proposed MAC protocols, analyzed the drawbacks of each protocol and proposed a new Delay adjust MAC protocol along with algorithm and analysis to improve the energy efficiency and looks forward for the new protocols their performances .
Acknowledgements
The authors are grateful to Er. K. Satyanaraya ,Chairman K.L.C.E for his constant encouragement towards Research in academics.
References
- S.S., Kulkarni, “TDMA services for Sensor Networks”, Proceedings of 24th International Conference on Distributed Computing Systems Workshops, 604-609 (2004).
- Pister k, Hohlt B, Jeong J, Doherty L, Vainio J P. Ivy ÿA sensor network infrastructure. 2003. http://www-bsac.eecs. berkeley.edu/projectes/ivy.
- A. El-Hoiydi, “Spatial TDMA and CSMA with preamble sampling for low power ad hoc wireless sensor networks”, Proceedings of ISCC 2002, Seventh International Symposium on Computers and Communications, Pages:685 – 692, 1-4 July (2002).
- W. Ye, J. Heidemann, D. Estrin, “Medium Access Control With Coordinated Adaptive Sleeping for Wireless Sensor Networks”, IEEE/ACM Transactions on Networking, 12(3): 493-506 (2004).
- T.V. Dam and K. Langendoen, “An Adaptive Energy-Efficient MAC Protocol for Wireless Sensor Networks”, The First ACM Conference on Embedded Networked Sensor Systems (Sensys‘03), Los Angeles, CA, USA, November (2003).
- G. Lu, B. Krishnamachari, C.S. Raghavendra, “An adaptive energyefficient and low-latency MAC for data gathering in wireless sensor networks”, Proceedings of 18th International Parallel and Distributed Processing Symposium, 224: 26-30 (2004).
- Joseph Polastre Computer Science Department University of California, Berkeley Jason Hill JLH Labs David Culler Computer Science Department University of California, Berkeley Versatile low power media access for wireless sensor networks, in: Proc. ACM SenSys, 2004. in sensys (2004).
- Guaranteeing the network lifetime in wireless sensor networks: A MAC layer approach Yongsub Nam a, Taekyoung Kwon b,*, Hojin Lee b, Hakyung Jung b, Yanghee Choi b a Information Networking Institute, Carnegie Mellon University, Pittsburgh, PA, USA b School of Computer Science and Engineering, Seoul National University, Seoul, Republic of Korea
- Investigating MAC Power Consumption in Wireless Sensor Network JAVIER BONNY Supervised by Jun LUO, Department of Communication Systems Swiss Institute of Technology (EPFL) Lausanne, Switzerland javier.bonny | jun.luo @epfl.ch February 7, (2005).

This work is licensed under a Creative Commons Attribution 4.0 International License.