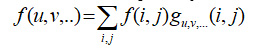Introduction
By definition, the biometric authentication may be defined as a security aspect which relies on the unique biological characteristics in order to verify the real person. The mechanism of the Biometric authentication systems is done by comparing the biometric captured data to the stored one in a database. Basically, the biometric authentication is used for managing any access to various resources. These various resources can be classified into two main categories: physical and digital resources. The resources can be computer device, smart phone, rooms, buildings, airport security, cars, etc. There various biometric authentication examples, the most common examples can be either finger print recognition or iris recognition. In the literature, there are many domains for biometric authentication. This paper focuses on the biometric exam authentication.1
Nowadays, there are many graduates from high schools and universities in different domains. Those graduates are looking for joining a university or looking for a job respectively. Joining a university for high school graduates or to finding a job for university graduates is competitive, therefore, choosing candidates among many applicants is judged by measuring the knowledge, skills, and the learning capabilities. Measuring it all is judged by conducting examinations. Examinations are classified into two main categories: the traditional paper based examinations, and the internet computer based examinations. The computer based examinations are widely used and adopted by a number of educational firms in various domains.1,2
The national center for assessment in Kingdom of Saudi Arabia, known as Qiyas, is a local center which was established to measure and evaluate the knowledge and skills by conducting various exams in different domains. The exams are classified into four main categories: the educational exams, the language exams, the vocational exams, and finally, the practice exams.2 Qiyas exams are conducting all over the Kingdom of Saudi Arabia. There are many Qiyas centers across the Kingdom of Saudi Arabia. The centers are mainly using the universities hall and computer labs.
According to the Qiyas website, there are various requirements for accessing the computer based exams. One of the requirements is showing the identification cards by the applicant. Actually, providing the identification is not robust enough in terms of candidate authentication. To overcome this drawback, a new model for enhancing the candidate authentication is proposed in this paper. The proposed model can be applied to any computer based examinations.
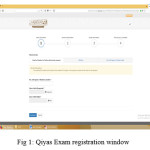
Qiyas exams candidates are applying for both paper based and computer based exams online using the Qiyas website. Firstly, the candidate needs to register as new users by creating a new account with user name and password. This mechanism is illustrated in figure 1.
After creating an account, the candidate continues his/her registration. Later on the candidate has to pay the exam fees in order to ensure his registration on a specific date and time. At this stage, the candidate goes to the exam based on his booking time where he/she needs to provide an identification card for authentication.2
Proposed System
In the literature, there are different systems using the user name and password as an authentication. There are advantages and disadvantages for those systems. The advantages of such systems underlies under that there are no additional hardware devices for bio-metric authentication such as scanning finger print device, cameras, etc. On the other hand, the disadvantages can be summarized as follows:
The security depends on the user’s ability of how to maintain the password mechanism.
The user’s password would be in security is in risk in the case of the user forgets his/her password.
Another security risk would occur, if the intruder gets the password where all username and password are saved.
Based on the above disadvantages, this paper proposed an enhancing technique to improve the authentication mechanism in internet computer based exams.4
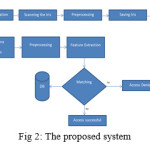
In this paper, the authentication process is enhanced by adding a bio-metric factor in order to make the authentication more robust. Basically, the candidate follows the traditional procedures for registering for Qiyas exam which is phase one. However, the candidate needs to go to any Qiyas center in the Kingdom of Saudi Arabia for scanning his/her eye iris. The candidate iris will be saved and presented in the computer server of the Qiyas center. Saving the iris will be with the candidate name and Saudi civil number. Later on, special pre-processing techniques will be implemented as proposed in.3 While, conducting the Qiyas exam, the candidate uses his user name and password to login to Qiyas exam. Here, before completing logging in to the Qiyas exam, the computer camera will scan the candidate iris and match it with the one in the Qiyas computer server. Based on successful matching, the candidate can access the exam otherwise, the screen will be locked which is phase two. It is noted that there are two main phases in the proposed system. First phase occurs while Qiyas exam registration. The main point in the first phase is to build and prepare the database for all candidates where each iris image is saved with the unique number of the candidate. The second phase consists of matching the captured iris image with the stored one. Based on true matching the candidate either performs the exam or not.3,4
In this paper, the proposed system uses the traditional recognition system phases: image acquisition, pre-processing, feature extraction, and classification. The proposed system is illustrated in figure 2.
Feature Extraction
The main goal here is to represent the candidate iris image in one dimensional vector to be mapped into a classifier for classification purpose. In the literature, there are many algorithms for extracting the features. Features are defined as the unique information extracted from the iris normalized image to be mapped into a classifier. There are two types of features: Structural and statistical features. The statistical features are used in this paper.
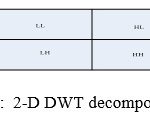
Discrete Wavelet Transform (DWT) is used to extract the features. Technically, the DWT is considered as hierarchical sub-band tool which is widely used in signal and image processing. Basically it is an interesting tool for extraction features from normalized pre-processed images. Here, the two dimensional DWT transform (2-D DWT) decomposes the normalized candidate input image into four sub-bands: the average component (LL), and the three detail components (LH, HL, HH) as shown in Figure 3.6
Basically, the sub bands are labeled as follows:
Both the horizontal and vertical low frequency components of the normalized iris image are represented by LL sub band.
Both the horizontal low and vertical high frequency components of the normalized iris image are represented by LH sub band.
Both the horizontal high and vertical low frequency components of the normalized iris image are represented by LH sub band.
Both the horizontal and vertical high frequency components of the normalized iris image are represented by HH sub band.
In this paper, extracting normalized iris image features is done using the 2d DWT, where the DWT coefficients are computed by
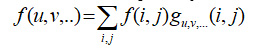
Where both i and j represents the spatial variables and both u, v represents the transform domain variables. The Haar wavelet transform is used to extract the DWT coefficient of the iris normalized image.6 Extracting the DWT coefficients is illustrated as follows:
in_img=Read the normalized iris image
// Compute the 2D DWT ( 4 levels decomposition)
[ca1 ch1 cv1 cd1]=dwt2( in_img,’haar’,4); 1st level
[ca2 ch2 cv2 cd2]=dwt2(ca1,’haar’,4);2nd level
[ca3 ch3 cv3 cd3]=dwt2(ca2,’haar’,4);3rd level
[ca4 ch4 cv4 cd4]=dwt2(ca3,’haar’,4);4th level
[ra ca]=siz(ca4);
features =reshape(ca4,1,ra*ca);
Classification
Generally, classification is classified as two categories: binary classification and multi class classification. The binary classification consists of two classes only, while the multi class classification consists of n classes. In classification, the input features will be mapped into a classifier.7,8
Furthermore, learning algorithms are classified into two main categories: the supervised learning and the unsupervised learning techniques. The supervised learning is simply the training mechanism of all inputs toward a specific label or target. On the other hand, the unsupervised learning the training mechanism of all inputs without a target. In unsupervised learning, a structure or relationships among different inputs is found. Based on learning algorithms, the classifier will be trained and tested. In this paper, the supervised learning is used.
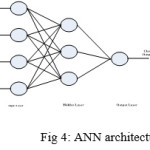
Classifying the iris image for any candidate is done by using the Artificial Neural Network (ANN). Basically, the ANN consists of a huge number of input neurons which are highly connected together for solving specific problems. Solving is done via learning the ANN by means of training and testing.7,8 The main architecture of ANN used in this paper is illustrated in figure 4.
The well-known example of the ANN architecture is applied in this paper. The feed forward network multi-layer perception (MLP) back propagation (BP) with supervised training is applied. By achieving the goal of minimizing an error, the BP algorithm is adjusted.7,8
Experimental Results
As mention earlier, the proposed system consists of two main phases. In phase one, uploading the candidate iris image is done by scanning the candidate iris after registration in any Qiyas center. After scanning the iris, it will be preprocessed and saved with the candidate unique identification number. In phase two, the candidate goes to the Qyiyas center to conduct the exam. Firstly, the candidate uses the computer to log in using his user name and password. Generally, the user name is the candidate unique identification number. After logging in, the process cannot be completed till the computer camera scans the candidate iris. Beyond scanning the candidate iris, the image is loaded into the server of the national center of assessments for matching purpose. Matching is done by comparing the current user name with the name of the iris image saved on the server of the national center of assessments. If the matching is approved, the screen will be opened for candidate and he/she can perform the exam. On the other hand, if the matching is failed, the screen will be locked and the candidate cannot perform the exam. Here, there are two security factors for authentication. The first one factor is achieved by logging into the Qiyas website by entering both user name and password. Also, the second one is achieved, which the core of this paper, by recognizing the iris of the candidate.
As mentioned earlier, the ANN consists of three main layers: the input layer, the hidden layer, and the output layer. The input layer receives the features extracted by DWT as an input. The hidden layer consists of neurons where the number of these neurons varies from 5 to 30. Finally, the output layer consists of 10 outputs. The features were mapped into the ANN classifier and the results are very good. Five experiments were done, and the recognition rate is taken out using the average of the five experiments. The recognition rate is 86.7%.
Conclusion
A new model framework for enhancing the authentication for internet computer based is proposed in this paper, The ANN classifier is used in the proposed system based on DWT features. The features are extracted using the DWT coefficients. The results of the proposed system and its performance based on ANN classifier are very good.
Acknowledgment
Sincere appreciation and thanks are expressed to TAIBAH University, College of Computer Science and Engineering (CCSE), Kingdom of Saudi Arabia for supporting this research.
References
- Arivoli, Ramu, “ A framework of Secure Biometric Based Online Exam Authentication: An Alternative to Traditional Exam”, International Journal of Scientific& Engineering Research. 2102;4(1).
- http://www.qiyas.sa/Sites/English/Pages/default.aspx
- Kanimozhi, k, Bio-metric Authentication for Online Examination, International Journal of Innovative Research in Computer and Communication Engineering. 2015;3.
- Jawad H. AlKhateeb, A Database For Identifying the Missed Pilgrims in Hajj and Umrah, International Journal of Computer and Information Technology (IJCIT), 2017;6(6).
- Bhagwager, Nirali, and Rathod, Yagnil, A survey on Iris Recognition for Authentication, International Journal of Technical research and Applications. 2015;3(2).
- Goslar, Vasundhara and Madankar, Mangala, Authentication System for Any Touch Devices Using DWT, International Journal of Engineering and Computer Science. 5(5):2016.
- Jawad H. AlKhateeb, Olivier Pauplin, Jinchang Ren, Jianmin Jiang, Performance of hidden Markov model and dynamic Bayesian network classifiers on handwritten Arabic word recognition, Knowledge-Based Systems. 2011;24:680-688.
CrossRef

This work is licensed under a Creative Commons Attribution 4.0 International License.