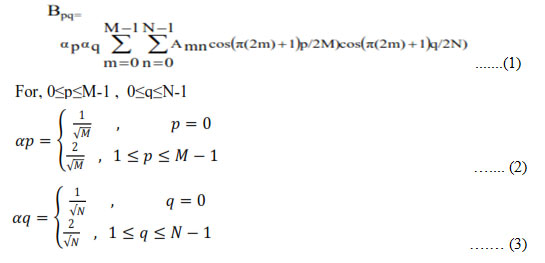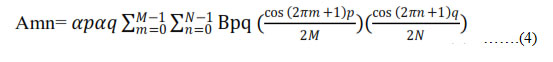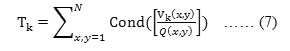A Robust DCT Based Digital Image Watermarking Using Fusion of Computational Intelligence Techniques
Introduction
In this world of digital, we can easily share pictures, video and text through the Internet which become most used resource. Due to the increased availability of digital data the transmission of multimedia data became daily routine nowadays. Therefore there is a pressing need to manage and protect the illegal duplication of data. Copyright protection or authentication of multimedia data has become critical issue due to massive spreading of broadband networks, easy copying, and new developments in digital technology. Nowadays, digital watermarking has become very popular as a good solution for copyright protection or authentication of multimedia content [12]. Digital watermarking is one kind of technique in which watermark is embedded into the host image, and it is extracted on the basis of requirement. The watermark can be anything like digital signal, pattern, logo, digital signature or biometric data which is inserted into a digital data to provide ownership of the authenticated users only. Digital watermarking can be classified based on several criteria like according to document- Image, Video, Text and Audio watermarking, according to human perception – invisible fragile, invisible robust, dual or visible watermarking, according to working domain – spatial and frequency domain. Spatial domain focuses on modifying pixels of one or two randomly selected subsets of images. Frequency domain is also called transform domain. In this domain values of certain frequencies are altered from their original. There are several common used transform domain methods, such as DCT, DWT, and DFT. Digital Watermarking (DW) based on computational intelligence (CI) is currently attracting considerable interest from the research community. Computational Intelligence is a sub-branch of Artificial Intelligence. Computational Intelligence (CI) is the study of adaptive mechanisms to enable or facilitate intelligent behavior in complex and changing environments. A system is called computationally intelligent if it deals only with numerical (low-level) data, has a pattern recognition component, and does not use knowledge in the AI sense. Many authors and researchers have identified Artificial Neural Networks, Evolutionary Computation, Swarm Intelligence, Artificial Immune Systems, Fuzzy Systems as five main paradigms of computational intelligence [1].
Literature Survey
B. Jagadeesh et al.[3] has proposed a back propagation neural network and HVS based digital image watermarking scheme. As neural networks are good at pattern recognition, they can be used as a medium to store the frequency domain components of the image and these can be used at the extraction of watermark. The watermarks bits are embedded into the mid frequency band of the DCT coefficients such that the host image is not distorted. The proposed model gives a better PSNR value and it is robust to many image processing attacks like compression, resizing, filtering etc. B. Jagadeesh et al.[5] has proposed a robust image watermarking based on DCT and BPNN using HVS. Neural networks are used in embedding the watermark and trained network is used in extracting the watermark. Neural networks adapt embedding strength to this algorithm. This algorithm is robust to several attacks. Charu Agarwal et al.[6] has proposed a novel image watermarking using Fuzzy-BP network. In this method Fuzzy-BP network is trained by 27 inference rules comprising of three input HVS features namely luminance sensitivity, edge sensitivity computed using threshold and contrast sensitivity computed using variance. Using this method high value of PSNR is generated which indicates that the signed image has good perceptible quality. Der-Chyuan et al[7] proposed a robust watermarking method based on the human visual model and the fuzzy inference system. By using the human visual model, the watermark can be adapted to different images that provide a maximum and suitable power watermark subject to the imperceptibility constraint. Hence, the capacity of the watermark can be larger, and it is hence more robust and imperceptible. Mukesh Motwani et al[9] has proposed watermarking based on human visual system model and the fuzzy inference system in wavelet domain.Fuzzy perceptual masks have been developed which allow high density and high energy watermarks. The fuzzy based watermarks are robust to attacks and at the same time achieve a high level of imperceptibility. N. Ramamurthy et al[10] has proposed the robust digital image watermarking algorithms using quantization in DWT domain using BPNN and DFIS. The advantage of the BPNN algorithm is that it provides better NCC for median filtering attack compared to DFIS model. That advantage of the proposed mamdani type fuzzy model is that the algorithm is robust to cropping, JPEG compression, salt & pepper noise, and rotation attacks compared to BPNN model. N. Ramamurthy et al.[11] has proposed image watermarking scheme in which watermark is embedded into the blue plane of the color image using 3-level DWT and BPNN. The proposed watermarking algorithm is imperceptible and robust to some normal attacks such as JPEG compression, salt and pepper noise, rotation and cropping. Pankaj U. Lande et al.[12] has proposed a fuzzy logic approach to embed the encrypted watermark for images in the wavelet domain. In this scheme only texture sensitivity is considered which is very simple to calculate. The experimental results show that the proposed scheme of wavelet based watermarking is imperceptible and robust against various attacks like noise additions and filtering. Sameh Oueslati et al[14] has presented a novel image watermarking approach based on the human visual system (HVS) model and Multi-Layer Feed- forward (MLF) neural network technique. The watermark was inserted into the middle frequency coefficients of the cover image’s blocked DCT based transform domain. The experimental results show that such method can survive of common image processing operations and has good adaptability for automated watermark embedding. Sameh Oueslati et al[15] has presented a new approach of blind watermarking scheme used in medical images. They have proposed a novel digital watermarking scheme in DCT domain based fuzzy inference system and the human visual system to adapt the embedding strength of different blocks. Experimental results show that the proposed scheme has good imperceptibility and high robustness to common image processing operators. Solaiman et al[16] proposed a new blind watermarking scheme in the frequency domain based on the HVS and the FIS. This technique can increase the robustness of watermarking images in terms of quality and confidentiality. This the method proves fragile compared to geometrical attacks while it resists JPEG attacks.
Preliminaries
Discrete Cosine Transform (DCT)
DCT represents the entire image as coefficients of different frequencies of cosines. The DCT of the image is calculated by taking 8×8 blocks of the image, which are then transformed individually. The DCT transforms a signal from a time domain representation to frequency domain representation. Embedding watermark into lower frequency coefficients will cause imperceptibility problems, embedding into higher frequency coefficients will not sustain to attacks such as compression etc, so to make algorithm more robust to known and unknown image processing attacks in this paper middle frequency coefficients are considered. Two dimensional DCT used in digital image processing for a given image A of size N*N is defined as [4,8,12]
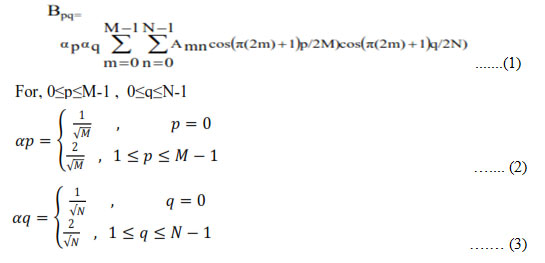
Where p varies from 0 to M-1 and q from 0 to N-1, M*N is size of original image. The DCT is invertible transform and its inverse is given by
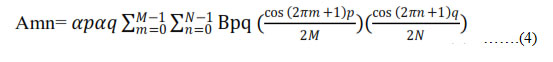
Human Visual System Model
The sensitivity of human eye to various spatial frequencies is determined by the frequency sensitivity. The effect of the imperceptibility to noise on a constant background is calculated by luminance sensitivity. We focus here on the sensitivity of brightness, texture and edge. The HVS model used in this work has been suggested in [14]. This model is also used in many insertion algorithm and detection of the watermark.
Edge Sensitivity
The edge is detected within the image using threshold operation. The edge sensitivity can be quantified as a natural corollary to the computation of the block threshold T. The MATLAB image processing toolbox implements graythresh() routine which computes the block threshold using histogram – based [11]. The implementation of this routine is as follows:
Ek = graythresh(f)….. ………(5)
Where, f is the host sub-image (block) and T is the computed threshold value
Luminance Sensitivity
Brightness masking proves to be effective towards detectable noise thresholds on a constant background. The brighter the background is, the larger the size of embedded signal. The luminance sensitivity is estimated by the following formula:
Lk = X DC,k / Mean(XDC) ……….(6)
Where X DC,k is the DC coefficient of the DCT of the kth block, XDC is the mean value of all DC coefficients of a specific image.
Texture Sensitivity
The stronger the texture is less visible is the watermark. The texture sensitivity can be estimated by quantizing the DCT coefficients of an image using the JPEG quantization table. The result is then rounded to nearest integers. The number of non-zero coefficients is then computed. This method can be calculated by the following formula:
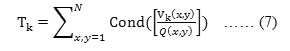
Where, (x,y) represents the location in the kth block and Cond(R)takes the rounded value of R and returns ‘1’ if the value is not equal to zero otherwise ‘0’ is returned.
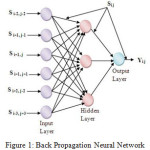
Back Propagation Neural Network
A neural network is a highly parallelized dynamic system with a directed graph topology which can receive the output data by means of response of its state on the input nodes. These are intended to abstract and model some of the functionality of the human nervous system in an attempt to partially capture some of its computational strengths. Neural networks are broadly two types, Feed forward and Feedback networks. Back propagation network is a feed forward network. There are three layers namely an input layer, hidden layers and an output layer. The desired outputs of Neural Network are the approximate DCT coefficients. Figure -1 shows the architecture of this network [1,3-6].
The first layer is to present the input variables to the network. Threshold sensitivity parameter is an input variable to the network, along with Fuzzy Inference System output. These inputs are then fed to a hidden layer using tan sigmoid activation functions which is fed to the output layer. This system does not fully replace humans but still they are needed to generate the training data and should check the results periodically to ensure the neural network is working at peak performance.
Fuzzy Inference System
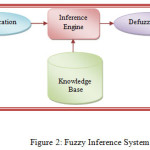
Fuzzy inference is the process of formulating the mapping from given input(s) to output(s) using fuzzy logic. The mapping them provides a basis from which decisions can be made, or patterns discerned. In general, a FIS is composed of four different function blocks namely a fuzzifier, a knowledge base, a fuzzy inference engine and a defuzzifier as shown in figure-2.[4]
Here Mamdani type DFIS is used to model the watermark weighting functions. Th
e human visual system parameters luminous sensitivity and Edge sensitivity are given as inputs to the Fuzzy inference system. Fuzzy Inference System technique is used to classify blocks which are more suitable to embed watermark based on fuzzy membership value.
Proposed Method
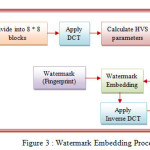
In proposed fuzzy-neuro based watermarking contains two modules: watermark embedding and extracting. In watermark embedding process, we input cover image having size 512*512 and thumbprint of size 64*64. Then perform RGB separation of cover image and select green plane. Then divide the green plane into 8*8 blocks and apply DCT on each sub image. Calculate HVS parameters like edge, luminous and text sensitivity. Give the luminous and edge sensitivity as inputs to the Fuzzy Inference System. Train the neural network for frequency sensitivity using FIS output and texture sensitivity as an input of neural network. These values are used in embedding process by doing so the frequency domain coefficients of the sub image are not varied by an unknown quantity instead replaced by one of the frequency sensitivity values, thus the blocks coefficients values remain unchanged even after inverse DCT is applied. At the extraction side the trained neural network along with FIS is used so as to obtain a similar set of data which is used to embed the watermark into the host image and by performing the DCT operation the watermark is extracted from the watermarked image.
Proposed Watermark Embedding Algorithm
Step 1: Read cover image and watermark (Fingerprint)
Step 2: Convert cover image into size of 512 * 512 and watermark into size of 64 * 64
Step 3: Separate R, G and B plane from the cover image and select green plane to embed the watermark
Step 4: Divide the green plane into 8*8 blocks and apply DCT for each sub image
Step 5: Calculate Luminous, Edge, Texture and Frequency sensitivity for each sub image
Step 6: Generate FIS values by developing FIS file with inputs Luminous and Edge sensitivity
Step 7: Train the neural network for frequency sensitivity using FIS output and texture sensitivity as an input of neural network.
Step 8: Embed watermark bit by following:
If w(c) ==1 then
X’= x + (NN(c) * w(c))
Else
X’ = x
Where w(c) = watermark bit, X’ = new DCT coefficients, x= DCT coefficients,
NN(c) = Neural Network output
Step 9: Take inverse DCT of each sub image
Step 10: combine new green plane with original red and blue plane to form watermarked image.
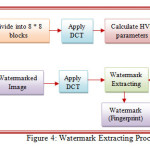
Watermark Extracting Algorithm
Step 1: Read cover image
Step 2: Convert cover image into size of 512 * 512
Step 3: Separate R, G and B plane from the cover image and select green plane to embed the watermark
Step 4: Divide the cover image into 8*8 blocks and apply DCT for each sub image
Step 5: Calculate Luminous, Edge, Texture and Frequency sensitivity for each sub image
Step 6: Generate FIS values by developing FIS file with inputs Luminous and Edge sensitivity
Step 7: Train the neural network for frequency sensitivity using FIS output and texture sensitivity as an input of neural network.
Step 8: Input Watermarked image and divide it into 8*8 blocks and apply DCT for each sub image
Step 9: Extract watermark by doing following:
If ( x’-x) / NN(c) >0
W’(c) =1
Else
W’(c) =0
Where W’(c) = watermark bit, x’ = DCT coefficients of watermarked image, x= DCT coefficients of original image, NN(c) = Neural Network output
Results
Here this experiment is performed on cover image “football.jpg” and fingerprint image is taken as biometric watermark. With proposed algorithm PSNR values for different two images are shown in below table I.
Table1: PSNR and MSE values for different cover image
|
Cover Image
|
MSE value
|
PSNR value
|
|
Lena.jpg
|
0.089569
|
58.64 db
|
|
Football.jpg
|
0.089760
|
58.63 db
|
|
Homework5.bmp
|
0.089668
|
58.64 db
|
Using above table, it has been clearly observed that this proposed method robust digital image watermarking using computational intelligence gives higher PSNR value as well as robust watermarked image compare to other methods. So the original image and watermark is shown in below figure-5 and watermarked image is shown in figure-6.
 |
Figure5: Original Cover image and finger print as watermark
Figure6: Watermarked Image and extracted watermark
Click here to View figure
|
Conclusion
In this paper, a robust digital image watermarking algorithm using computational intelligence is proposed. Here fuzzy-neuro system is used for embedding and extracting the watermark in cover image. Here fingerprint is used as a watermark which is embedded in the mid frequency band of the DCT coefficients. In the embedding process the fuzzy-neuro system is used to remember the watermark embedding weights and to retrieve the watermark bits at extracting process. The experimental results show that the proposed algorithm embeds the finger print in such a way that the host image is not distorted and generates robust watermarked image having good PSNR value. In future we will use other medium as host or cover like video, audio and text with DWT based digital watermarking using computational intelligence technique.
References
- Akerekar R. A., S. P. (2009). Knowledge-based Systems. Sudbury,MA, USA: Jones and Bartlett.
- Ashraf Darwish, A. A. (2008). The Use of Computational Intelligence in Digital Watermarking: Review, Challenges, and New Trends. ICS AS CR .
- B.Jagadeesh, D. K. (2014). Robust Digital Image Watermarking Scheme based on DCT and BPNN. International Journal of Advanced Research in Electrical, Electronics and Instrument Engineering , 3 (5).
- B.Jagadeesh, D. P. (2014 ). Fuzzy-Neuro based Robust Digital Image Watermarking Technique. International Journal of Advanced Research in Computer and Communication Engineering , 3 (7).
- B.Jagadeesh, P. M. (2013). HVS based Robust Image Watermarking in DCT Domain using Neural Networks. International Journal of New Trends in Electronics and Communication , 1 (2).
- Charu Agarwal, A. M. (2010, October). A Novel Image Watermarking Technique Using Fuzzy-BP Network. Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP) , 102-105.
- Der-Chyuan Lou, T.-L. Y.-C. (2004). Robust Digital Watermarking Using Fuzzy Inference Technique. JOURNAL OF C.C.I.T. , 32 (2).
- Monika Patel, D. P. (2013). Analysis and Survey of Digital Watermarking Techniques. International Journal of Advanced Research in Computer Science and Software Engineering, Vol 3, Issue 10 .
- Mukesh Motwani, F. C. (2009, July). Fuzzy Perceptual Watermarking For Ownership Verification. Proceedings of the 2009 International Conference on Image Processing, Computer Vision,and Pattern Recognition , 13-16.
- Nallagarla Ramamurthy, D. (2012). Robust Digital Image Watermarking Scheme with Neural Network and Fuzzy Logic Approach. International Journal of Emerging Technology and Advanced Engineering , 2 (9).
- Nallagarla Ramamurthy, S. V. (2013). The Robust Digital Image Watermarking Scheme With Back Propagation Neural Network in DWT Domain. IJCSNS International Journal of Computer Science and Network Security , 13 (1).
- Pankaj U.Lande, S. N. (2010). A FUZZY LOGIC APPROACH TO ENCRYPTED WATERMARKING FOR STILL IMAGES IN WAVELET DOMAIN ON FPGA. International Journal of Signal Processing, Image Processing and Pattern Recognition , 3 (2).
- Rafel C. Gonzalez, R. E. (2002). Digital Image Processing Using MATLAB. 406-467.
- SAMEH OUESLATI, A. C. (2011). ADAPTATIVE IMAGE WATERMARKING SCHEME BASED ON NEURAL NETWORK. International Journal of Engineering Science and Technology (IJEST) , 3 (1).
- Sameh Oueslati, A. C. (2010). MAXIMIZING STRENGTH OF DIGITAL WATERMARKS USING FUZZY LOGIC. Signal & Image Processing : An International Journal , 1 (2).
- Solaiman, S. O. (2011). A Fuzzy Watermarking Approach Based on the Human Visual System. International Journal Of Image Processing (IJIP) , 4 (3).
- YU Chang-hui, F. W.-l. (2011). The Digital Watermarking Technology based on Neural Networks. IEEE , 11, 5-8.
CrossRef

This work is licensed under a Creative Commons Attribution 4.0 International License.