Dharmesh Bhatt* and Bijendra Agrawal
Janardhan Rai Nagar Rajasthan Vidhyapeeth, Udaipur- 313001, Rajasthan, India.
Corresponding Author Email: bhatt_dh123m@yahoo.com
DOI : http://dx.doi.org/10.13005/ojcst/10.02.23
Article Publishing History
Article Received on :
Article Accepted on :
Article Published : 09 May 2017
Article Metrics
ABSTRACT:
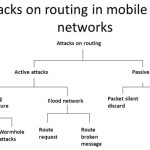
In the unknown environment of network the security the major issue for safe communication between the nodes. In such networks a lot of active and passive attacks are done by the attackers in groups in the data packets and routing messages. Mobile Adhoc networks are such type of networks which does not have any centralized authentication and the nodes communicate with each other. In MANET security plays a vital role for safe communication. The focus is given on security of Mobile Adhoc Networks. MANET is open network which is available for the malicious and trustworthy users to communicate. The MANET has to design a robust solution which deals with such type of malicious attackers so that a health network transmission takes place between trustworthy nodes. The Mobile Adhoc Networks are the network which works in isolation along with the wired infrastructure. This elasticity of MANET is its biggest strength but it is also a big vulnerability for security issues. In paper we will discuss the active and passive attacks including black hole attacks, spoofing, warm hole, flooding and traffic monitoring, traffic analysis and eavesdropping respectively.
KEYWORDS:
MANET; Intrusion Detection; Attacks; Security; AODV
Copy the following to cite this article:
Bhatt D, Agrawal B. Crack Failure Analysis of Scaffolding Frame Intersection using ADINA. Orient.J. Comp. Sci. and Technol;10(2)
|
Copy the following to cite this URL:
Bhatt D, Agrawal B. Crack Failure Analysis of Scaffolding Frame Intersection using ADINA. Orient. J. Comp. Sci. and Technol;10(2). Available from: http://www.computerscijournal.org/?p=5691
|
Introduction
MANET is an assembly of affordable, small and strong devices. MANET is rapidly growing network. MANET is adaptive and self organizing in nature. Devices are connects with each other and performs communication for sharing of data and services. Adhoc networks allow device to maintain their connection and facilitate to remove or adding devices from network. The topology of ADHOC networks are also not stable it changes rapidly and unpredictably over time.
There is no central authorization or centralized infrastructure to maintain the connections. Due to the absence of centralized authorization and fluctuate topology the message routing is a big problem but the message delivery are executed by the nodes themselves. In the static networks the packet is route from source to destination which is based on shortest path and given cost of function but to extend this method in MANET is difficult. There are miscellaneous set of applications depend on ranging from large-scale to small and mobile networks to high dynamic networks static networks for MANET that are controlled by power sources. From past few decades the MANET are popularly increasing particularly within 1990s. The mobility and wireless devices are increased rapidly and adapted. Some critical challenges and open challenges in MANET are still exists and which are yet to be solved.
Characteristics of MANET
- MANET is self-sufficient in nature in which each node is host and router.
- MANET has no centralized authentication. Distributed nature is adapted by MANET for the operation of host configuration, routing and security.
- There is dynamic topology in the MANET. Nodes are free to add or remove from the network anytime.
- Multi hope is good characteristics of MANET. When the source node and destination node are not in radio range, the multi hop routing has a option in MANET
- Less human intervention is required in the MANET due to its mobile and spontaneous behavior
- A symmetric environment is created by the nodes of MANET which have similar feature, responsibility and capability.
- In the comparision of the wired networks the wireless network has less reliability, capacity, efficiency and stability.
Application of MANET
The application of MANET includes:
Military Area
Mobile Adhoc Network plays an important role in military. Due to presence of common place network technology military has great advantage to maintain the information and communication between the solider, vehicles and other important data communication
Mutual work
In offices and business environment for the communication between the officials where collaborative computing needed outside office environment than inside and they want to communication with each other or sharing data or files on the given project. MANET might play a vital role in such environment.
Local level
To spread and share information among the students or in the conference MANET will become very useful which links them by using notebook computers. The home networks are also an appropriate level where the devices connect with each other and communicate with each other by sharing data and other information.
Short range Communication
MANET is a good choice for short range communication in which the nodes are resemblance with a person and communicate with each other in short radio range. Communication between the mobile devices and laptop or a mobile phone is simplified by Bluetooth. Bluetooth is a short-range communication MANET where devices connect with each other and share their information.
Emergency
At the time of emergency MANET can be use for the source of communication where other communication may be damaged or non-existence of communication networks. Flood, Fire or earthquakes are the disasters and for the rescue operation MANET can be used during non availability of any network.
Issues and Challenges of MANET
Limited Bandwidth
The wireless networks have a limited bandwidth in comparison to the wired networks. Wireless link has lower capacity as compare to infrastructure networks. The effect of fading, multiple accesses, interference condition is very low in ADHOC networks in comparison to maximum radio transmission rate.
Dynamic topology
Due to dynamic topology the nodes has less truest between them. I some settlement are found between the nodes then it also make trust level questionable.
High Routing
In ADHOC networks due to dynamic topology some nodes changes their position which affects the routing table.
Problem of Hidden terminal
The Collision of the packets are held due to the transmission of packets by those node which are not in the direct transmission range of sender side but are in range of receiver side.
Transmission error and packet loss
By increasing in collisions , hidden terminals, interference, uni-directional links and by the mobility of nodes frequent path breaks a higher packet loss has been faced by ADHOC networks.
Mobility
Due to the dynamic behavior and changes in the network topology by the movement of the nodes .ADHOC networks faces path breaks and it also changes in the route frequently.
Security threats
New security challenges bring by Adhoc networks due to its wireless nature. In Adhoc networks or wireless networks the trust management between the nodes leads to the numerous security attacks.
MANET’s
These two types of attacks are different in nature illustrate below:
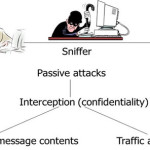
Passive Attacks
The eavesdropped in the passive attacks which violets confidentiality. This packet contains the confidential information. Attacker attacks on the data exchanged doing any alteration. Confidential attribute of the system is targeted by this attack. It is very difficult to find out the passive attacks because it could not affect the operation of the network. Passive attacks are usually used to know the information about the network or the communication patter between the communicating parties. It is easy to launch.
Issues and Challenges of MANET
Limited Bandwidth
The wireless networks have a limited bandwidth in comparison to the wired networks. Wireless link has lower capacity as compare to infrastructure networks. The effect of fading, multiple accesses, interference condition is very low in ADHOC networks in comparison to maximum radio transmission rate.
Dynamic topology
Due to dynamic topology the nodes has less truest between them. I some settlement are found between the nodes then it also make trust level questionable.
High Routing
In ADHOC networks due to dynamic topology some nodes changes their position which affects the routing table.
Problem of Hidden terminal
The Collision of the packets are held due to the transmission of packets by those node which are not in the direct transmission range of sender side but are in range of receiver side.
Transmission error and packet loss
By increasing in collisions , hidden terminals, interference, uni-directional links and by the mobility of nodes frequent path breaks a higher packet loss has been faced by ADHOC networks.
Mobility
Due to the dynamic behavior and changes in the network topology by the movement of the nodes .ADHOC networks faces path breaks and it also changes in the route frequently.
Security threats
New security challenges bring by Adhoc networks due to its wireless nature. In Adhoc networks or wireless networks the trust management between the nodes leads to the numerous security attacks.
MANET’s
These two types of attacks are different in nature illustrate below:
Passive attacks
The eavesdropped in the passive attacks which violets confidentiality. This packet contains the confidential information. Attacker attacks on the data exchanged doing any alteration. Confidential attribute of the system is targeted by this attack. It is very difficult to find out the passive attacks because it could not affect the operation of the network. Passive attacks are usually used to know the information about the network or the communication patter between the communicating parties. It is easy to launch.
Some other major challenges in MANET
Some other challenges of the MANET are describe briefly as below:
Dynamic topologies
In Dynamic Topology the nodes are free to move in any direction. Topology of network changes rapidly and unpredictably by the time. Due to this topology the bidirectional and unidirectional routing exists. Challenging task is to transferring the packets between the nodes because the topologies are changes continuously.
Multicast Routing
Another challenge of MANET is multicast. The multicast dynamic this networks because the nodes are randomly changes its position. The nodes have multiple hopes instead of single hop and they are complex. The new device adds in the network need to know all the other nodes. To facilitate automatic optimal route selection dynamic update is necessary due to existence of node
Variability in capacity links due to Bandwidth Constraint
Being a link of wireless they continue with low capacity in comparison to the hardwired.
Power-constrained and operation
This is also considered as a challenge for the MANET network. The MANET is a network where all nodes rely on the batteries or some exhaustible source of energy. Conversion in the energy is the optimized criteria and an important system design. Lean power consumption is also used for the light weight mobile terminals. Conservation of power and power-aware routing is another aspect which must be considered.
Security and Reliability
Nasty Neighbor relaying packets is also a security problem alongwith other vulnerabilities connected. Different schemes are used for authentication and key management in distributed operations. Reliability problem is also a wireless link characteristic due to limited wireless transmission. Due to the broadcast of wireless medium packets loss and errors in the data occur. In comparison to the wired network the wireless networks are more vulnerable to security threats.
Quality of Service
In MANET the environment will change constantly so that it provides different quality of service levels which are challengeable. The random nature in the quality communication of MANET it is difficult to server good guarantee of service of the device. To support multimedia services adaptive Quality of Services can be implement over traditional resources.
Inter-networking
Communication with fixed networks is also expected from MANET in many cases. The existence of routing protocols in both the networks is quite challengeable for pleasant mobility management.
Multicast
Multicast stands for multiple communication between wireless devices. As the nature the multicast is not remains for longer period so that the protocol has to maintain mobility which includes the leaving and joining of nodes.
Diffusion hole problem
The excess energy consumption is faced by the nodes which are present in the boundaries of the holes. If the bypass holes are wish to omit then the packets are delivered along the hole boundaries. This enlarges the hole due to consumption of very much of the nodes and its boundaries.
Conclusion
In this paper we discuss many vulnerability and challenges in MANET. MANET has no centralized infrastructure and due to continuous changes in the topology the chances of attacks are increased in such type of network. The attacks are classified into two parts i.e. active and passive attacks then after some other challenges are also discussed. The application are use to prevent such attacks but an algorithm must be introduced to prevent such attacks at which is based on the layers.
References
- Mobile Adhoc Network (MANET). Routing Protocol Performance Issues and Evaluation Considerations. URL: http://www.ietf.org/rfc/rfc2501.txt
- S. Basagni et al., Mobile Ad Hoc Networking, IEEE Press and John Wiley and Sons, 2003.
- Conti, M.; Maselli, G.; Turi, G.; Giordano, S.; , “Cross-layering in mobile ad hoc network design,” Computer , vol.37, no.2, pp. 48- 51, Feb 2004, doi: 10.1109/MC.2004.1266295 URL: http://ieeexplore.ieee.org/ stamp/stamp.jsp?tp= andarnumber = 1266295andisnumber=28321
CrossRef
- Chakrabarti, S.; Mishra, A.;, “QoS issues in ad hoc wireless networks,” IEEE Communications Magazine, vol. 39, no.2, pp.142-148, Feb 2001, doi: 10.1109/35.900643 URL: http://ieeexplore.ieee.org/ stamp/stamp.jsp?tp=andarnumbe r=900643andisnumber =19494
CrossRef
- Royer, E.M.; Chai-Keong Toh; , “A review of current routing protocols for ad hoc mobile wireless networks,” IEEE Personal Communications, vol.6, no.2, pp.46-55, Apr 1999, doi: 10.1109/98.760423 URL: http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=andarnumber= 760423andisnumber=16455\
CrossRef
- J. Macker, ”Mobile Ad hoc Networking (MANET): Routing Protocol Performance Issues and Evaluation Considerations”. IETF RFC 2501, January 1999.
- Mohammed Saeed Al-kahtani, “Survey on Security Attacks in Vehicular Ad hoc Networks (VANETs),” IEEE 2012.
- Gagandeep, Aashima, Pawan Kumar,“ Analysis of Different Security Attacks in MANETs on Protocol Stack A-Review”, International Journal of Engineering and Advanced Technology (IJEAT) ISSN: 2249 – 8958, Volume-1, Issue-5, June 2012.
- Priyanka Goyal, Sahil Batra, Ajit Singh “A Literature Review of Security Attack in Mobile Ad-hoc Networks”, International Journal of Computer Applications (0975 – 8887) Volume 9– No.12, November 2010

This work is licensed under a Creative Commons Attribution 4.0 International License.