Gaurav Kumar Singh Gaharwar1, 2, V. V. Nath3, Raina Gaharwar4
1Research and Development, Raksha Shakti University, Ahmedabad, (India)
2School of Business and Law, Navrachana University, Vadodara,(India)
3Institute of Management, Nirma University, Ahmedabad, (India)
4G. H. Patel Department of COMPUTER SCIENCE and Technology, Sardar Patel University, Vallabh Vidyanagar, (India)
DOI : http://dx.doi.org/10.13005/ojcst/901.03
Article Publishing History
Article Received on :
Article Accepted on :
Article Published : 13 Feb 2016
Article Metrics
ABSTRACT:
Image forgery is always been sought after field of digital forensics, as it becomes very convenient now to edit/forge any image with many desktop based and online tools available. Also, to prove authenticity of any image in the court of law, there is a need of algorithm which can used to check forgery of any image, irrespective of its forgery type. Proposed model in the paper aims to provide neuro-fuzzy based algorithm which utilizes capabilities of best algorithms for each type and provides accurate result about the forgery in the image. It also provides analysis about type of forgery in the image along with the area forgered in the image.
KEYWORDS:
Image forgery; Copy-move forgery; Image splicing; Image retouching; Lightning condition; Neuro-fuzzy approach; ANN
Copy the following to cite this article:
Gaharwar G. K. S, Nath V. V, Gaharwar R. Neuro-Fuzzy Based First Responder for Image Forgery Identification. Orient.J. Comp. Sci. and Technol;9(1)
|
Copy the following to cite this URL:
Gaharwar G. K. S, Nath V. V, Gaharwar R. Neuro-Fuzzy Based First Responder for Image Forgery Identification. Orient. J. Comp. Sci. and Technol;9(1). Available from: http://www.computerscijournal.org/?p=3196
|
Introduction
Image forgery
Image forgery is to manipulate the content of an image in such a way that either it hide an important part of the image or represents wrong information. Image forgery is very common of digital crimes carried out. The most familiar targets of these forgeries are photographs, legal or administrative documents and financial documents line checks. Nowadays it becomes effortless to manipulate any digital image with readily available software like Adobe Photoshop. Digital image forgery can be identified into two categories viz. cloning in which an area of the image is pasted on the same image, and composition in which an area of the image contain area from some other image.
 |
Figure 1: show how and image can be easily forged where Wong Su En from DAP-China forged a photograph receiving knighthood from Queen Elizabeth-II.
Click here to View figure
|
Different types of Image forgeries
Image forgeries can be categorized into copy-move forgery, image splicing, image retouching, and lightning condition.
“In copy-move forgery, the area copied belongs to the same image, the dynamic range and color remains will be same as the other part of image. Copy-move forgery is usually done to either hide some part of the image of to show some part of the image multiple times.” [1] This is most common type of image forgeries.
“Image splicing forgery involves composition or merging of two or more images changing the original image significantly to produce a forged image.” [1] Whenever images with similar looking background are merge, then becomes extremely difficult to find forgered image.
“In Image Retouching, the images are less modified. It just enhances some features of the image. There are several subtypes of digital image retouching, mainly technical retouching and creative retouching.” [2]
“Many times the image splicing is done with such a precision that it is visually impossible to identify different lightning conditions in the combined image. To the extent that the direction of the light source can be estimated for different objects/people in an image, inconsistencies in the lighting direction can be used as evidence of digital tampering.” [3]
Different Image forgery identification techniques
There are different methods suggested by different researchers for solving different types of forgeries, viz copy-move forgery, image splicing, image retouching, and lightning condition.
Copy-move forgery identification methods can be categorized into either block based method or keypoint based method. [4] Block based methods gives accurate result for identifying image forgery in any jpg image but also takes lot more time then keypoint based methods. [5] And forgery covered under geometric transformations like rotation and scaling are better suited for the keypoint based methods while methods like exhaustive block search method can find almost any type of copy-move forgery. [4]
Image splicing forgery detection algorithm divided into two categories: detection algorithm based on authenticity of the local area and detection algorithm based on source inconsistency. [4] There are many algorithms proposed by different researchers for exploiting inconsistency local characteristic of an forgered image. It is extremely difficult for any image forger to hide these inconsistencies. Also, image source in always ideal, it has its own inconsistencies, these inconsistencies are then pass on to all the images taken from that source. Consistency in the inconsistencies of source is used for identifying image splicing forgery.
Image retouching algorithms work on analyzing image histogram to identity contrast enhancement. Irregularities from the histogram can be considered as the evidence of image retouching forgery. With histogram analysis algorithm can also localize the forgery area. [4] Image retouching is frequently done highlight certain part of an image, e.g. one might modify the color of faces in the photograph.
Lightning inconsistency is one of the obvious techniques to identify image forgery. Many algorithms use 2-D surface normals, and lateral chromatic aberration. Many algorithms use Peak/Gap bin detection method for identifying lighting inconsistencies. [4] Whenever there is huge mismatch in the contrast of different parts of an image, this type of forgery can be a great possibility.
Limitations with existing techniques
There are many different types of image forgeries and many different algorithms are given by researchers to detect forgery. In single forgery type also many algorithms are there working on completely different principles. The result is also inconsistent and different if different algorithms are applied on same forgered image. There is no single method/algorithm for image forgery identification.
Due to which there is always a need of expert to identify first type of forgery and then apply appropriate algorithm to check forgery. As it is subjective assessment by expert about the type of forgery, this becomes a grey area in image forgery identification. There is a need of an algorithm which can predict any type of forgery in an image.
Proposed model
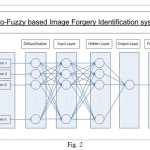
The proposed system will utilize advantages of different algorithms. The forged image is sent to different algorithms which then analyzed result is then given in the form of whether the image is forgered according to that algorithm of not. The fuzzification of this true-false values are done before inputting to input layer of the Artificial Neural Network (ANN). Inside the ANN different weights are assign to different connections and accordingly knowledge has been generated at the output layer of ANN. Lastly defuzzification of the output knowledge is been done to provide yes-no answer to the user.
 
Inherent property of any computer system is its speed and accuracy and with the better hardware coming to market every month, the speed will be ever increasing in future. With better speed the expert system will leverage the benefits of many algorithms and provide user accurate result which can withstand in the court of the law. Also, model utilizes capabilities of best of the forgery detection algorithms with the help of ANN. If ANN is trained correctly then most of the forgeries can be identified effortlessly.
Neuro-fuzzy approach
Learning capabilities of neural networks is great for numerical data but real world, which is not always numeric data, deals largely with fuzzy data. On the other hand fuzzy logic has a good interpretation capability. Neuro-fuzzy is a hybrid approach to leverage the capabilities of both neural networks and fuzzy logic. The output of one system can be supplied as the input of the other system. The cooperative neuro-fuzzy model corresponds to the case that one system is used to adapt the parameters of the other system [6].Neuro-fuzzy model takes the form of either a fuzzy neural network or a neuro-fuzzy system. A hybrid neuro-fuzzy system does not use multiplication, addition, or the sigmoidal function, but uses fuzzy logic operations such as -norm and -conorm.
A fuzzy neural network is a neural network equipped with the capability of handling fuzzy information, where the input signals, activation functions, weights, and/or the operators are based on the fuzzy set theory [7].A neuro-fuzzy system is a fuzzy system, whose parameters are learned by a learning algorithm. It has a neural network architecture constructed from fuzzy reasoning, and can always be interpreted as a system of fuzzy rules. Learning is used to adaptively adjust the rules in the rule base, and to produce or optimize the membership functions of a fuzzy system. Structured knowledge is codified as fuzzy rules. Expert knowledge can increase learning speed and estimation accuracy. Both fuzzy neural networks and neuro-fuzzy systems can be treated as neural networks, where the units employ the -norm or -conorm operator instead of an activation function. The hidden layers represent fuzzy rules.
Advantages of proposed model
The proposed system will be developed in the domain of digital forensics and serve as first responder in the case of identifying forgery or tempering in the image. Data collected during this process is used to train the neurons for improving the process for successive executions.
The proposed system will not eliminate than need of expert, but it will assist an expert by automating first responder processes so expert can focus on more important tasks where his involvement is highly required. Human resource is most critical resource in any organization for performing certain task, in digital forensics the situation is more critical due to less availability of experts. So, it becomes more important not to use these experts for routine task like first responder process and this routine task can be performed by intelligent computerized systems like expert system.
Conclusion
The proposed expert system will combine the power different image forgery algorithms for verifying authenticity of the image on the hand. The simple to use tool will facilitate novice to find out forgery from the image in the absence of forensic expert. The simple to use system will not only provide result in simpler format but also due the processing with multiple algorithms it will provide more accurate analysis of any image.
References
- G. K. S. Gaharwar, V. V. Nath, and R. D. Gaharwar, “COMPREHENSIVE STUDY OF DIFFERENT TYPES IMAGE FORGERIES,” in International conference on Recent Advances in Engineering Science and Management, New Delhi, 2015, pp. 345-350.
- P. Sabeena Burvin and J. Monica Esther, “Analysis of Digital Image Splicing Detection,” IOSR Journal of Computer Engineering, vol. 16, no. 2, pp. 10-13, Mar-Apr 2014.
CrossRef
- Micah K. Johnson and Hany Farid, “Exposing digital forgeries by detecting inconsistencies in lighting,” ACM Multimedia and Security Workshop, 2005.
CrossRef
- Gauravkumarsingh Gaharwar, V. V. Nath, and Raina Gaharwar, “Comprehensive Study of Contemporary Image forgery Identification Techniques,” International Journal of Computer Science and Information Technology, vol. 6, no. 6, pp. 5413-5416, December 2015.
- V S Kulkarni and Y V Chavan, “Comparison of methods for detection of Copy-Move Forgery in Digital Images,” Spvryan’s International Journal of Engineering Sciences & Technology, vol. 1, no. 1, October 2014.
- Stephan I Gallant, “Connectionist expert systems,” Communications of the ACM, vol. 31, no. 2, pp. 152-159, February 1988.
CrossRef
- W. Pedrycz and A F Rocha, “Fuzzy-Set Based Models of Neurons and Knowledge- Based Networks.,” IEEE Trans. Fuzzy Systems, vol. 1, no. 4, pp. 254-266, 1993.
CrossRef

This work is licensed under a Creative Commons Attribution 4.0 International License.