Manohar Koli1, S. Balaji2, Ravi kumar H. Roogi3, Deepak .Marigoudar4, Priya Nayak5
1Dept. of Computer Science, Karnataka University Dharwad, Karnataka, India.
2Dept. of CSE, City Engineering College Bangalore-560061, Karnataka, India
Article Publishing History
Article Received on :
Article Accepted on :
Article Published : 06 Sep 2014
Article Metrics
ABSTRACT:
Intensive research has been carried out and is still taking place in the field of detection of counterfeit money. This area of research plays a vital role in the maintenance of consistency in economy and also crime -free society by detecting counterfeit money.
In this paper we have proposed a system for automatic detection of counterfeit notes. This paper is based on the fact that all notes are printed with unique serial number. Every person who is currently using the note for transaction has to register the serial number of the note in his account along with his unique identity number. This serial number is used for validating the notes and data base transactions.
KEYWORDS:
Mobile based system; counterfeit money
Copy the following to cite this article:
Manohar Koli M, Balaji S, H. Roogi R. K., Marigoudar D, Nayak P. A New Mobile Based System to Detect Counterfeit Money. Orient. J. Comp. Sci. and Technol;7(2)
|
Copy the following to cite this URL:
Manohar Koli M, Balaji S, Roogi R. H, Marigoudar D, Nayak P. A New Mobile Based System to Detect Counterfeit Money. Orient. J. Comp. Sci. and Technol;7(2). Available from: http://www.computerscijournal.org/?p=1248
|
Introduction
Counterfeit money is currency that is produced without the legal sanction of the state or government to resemble some official form of currency closely enough that it may be confused for genuine currency. Producing or using counterfeit money is a form of fraud.
Some of the ill-effects that counterfeit money has on society are:
- Reduction in the value of real money.
- Increase in prices (inflation) due to more money getting circulated in the economy – an unauthorized artificial increase in the money supply.
- Decrease in the acceptability (satisfactoriness) of money – payees may demand electronic transfers of real money or payment in another currency (or even payment in a precious metal such as gold).
- Companies are not reimbursed for counterfeits. This forces them to increase prices of commodities.
At the same time, in countries where paper money is a small fraction of the total money in circulation, the macroeconomic effects of counterfeiting of currency may not be significant. The microeconomic effects, such as confidence in currency, however, may be large.
In the late twentieth century advances in computer and photocopy technology made it possible for people without sophisticated training to easily copy currency. In response, national engraving bureaus began to include new more sophisticated anti-counterfeiting systems such as holograms, multi-colored bills, embedded devices such as strips, micro printing and inks whose colors changed depending on the angle of the light, and the use of design features such as the “EURion constellation” which disables modern photocopiers. Software programs such as Adobe Photoshop have been modified by their manufacturers to obstruct manipulation of scanned images of banknotes.
Proposed System
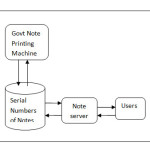
In this paper we are presenting a new proposed system for the detection of counterfeit money. This Proposed System is three layer architecture. The front end comprises of persons who are using the notes for transaction. The middle layer comprises of a Note Server which manages transactions and back end is a data base contains serial number of all notes and information about the users.
System Configuration
Front end
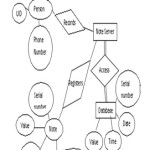
The front end contains a registration module where the person who lends the money will be registered as old owner and the person who receives the money will be registered as new owner. Then the person who lends the money will delete his old database record. For all above purpose the user uses their unique identity numbers. The new entry can be made by any new person by entering his/her unique identity number, serial number and value of the note and identity number of old and new owner.
Registration
Acknowledgement
Middle Layer
The middle layer consists of a note server which manages and maintains the record of each and every transaction. This record is helpful in validating the real notes.
Back end
The back end consists of huge database which contains the serial number of all the notes that has been printed.
Experimental Analysis
Easy way to detect the money which has been lost
Suppose the person has lost some amount of money which comprises of notes from X serial number to Y serial number. He has to register the serial numbers lost. So, no other person who has got that money which comprises of notes of same serial number cannnot register, as he is not having the valid old owner id(because he will not be knowing the old owner as he got the money in illegal way).
Solution to detect the counter feit money
Each note contains unique serial number. So if there is any double entry of the same serial number, it is obivious that one of the note must be duplicate or fake. So counterfeit money can be easily detected.
Curruption can be controlled
A person should register each and every transaction. So each transaction details are obtained which helps to detect the time and the person who has done the illegal transaction such as curruption.
Economy of the country can be analysed
Each trasaction details are registered. So the economy of the country can be analysed by accessing the database.
Conclusion
The proposed method is a robust method to detect the counterfeit money. The proposed method which provides secured environment is very easy to implement and also less in cost. It even simple and user friendly.
References
- KEEGAN, D, “Foundations of Distance Education”, Routledge, 3rd edition, 1996.
- DAY, B, “Developing Wireless Applications with J2ME Technology”, URL:http://wireless.java.sun.com/getstart/articles.
- MUCHOW, J, “Core J2ME Technology and MIDP”, Prentice-Hall, 2001.
- GUIGERE, E, “J2ME Tech Tips – Client-Server Communication over HTTP Using MIDP and Servlets”, URL: www.microjava.com/developer/resource_articles.
- PRADO, A, F, “Desenvolvimento de Software Baseado em Componentes (DBC)”. URL: http://www.recope.dc.ufscar.br/engenhariadesoftware/principa/index.htm.
- D’SOUZA, D, F., WILLS, A, C, – “Objects, Components and Frameworks with UML: the Catalysis Approach”, Addison-Wesley Pub Co, 1998.
- JACOBSON, L, BOOCH, G, RUMBAUGH, J, – “The Unified Software Development Process”, Addison-Wesley Pub Co, 1999.
- QUINN, A, “Trail: JavaBeans”, URL: http://java.sun.com/docs/books/tutorial/javabeans/.
- SUN MICROSYSTEMS, “How To Write Your First JES Service”, URL:http://java.sun.com/j2me/docs/pdf/tutorialsol.pdf.

This work is licensed under a Creative Commons Attribution 4.0 International License.