Iqra Altaf Mattoo and Parul Agarwal*
Department of Computer Science, Jamia Hamdard, Hamdard Nagar, New Delhi, 110062, India
Corresponding author Email: parul.pragna4@gmail.com
DOI : http://dx.doi.org/10.13005/ojcst/10.02.35
Article Publishing History
Article Received on :
Article Accepted on :
Article Published : 20 May 2017
Article Metrics
ABSTRACT:
Biometric Recognition is the most suitable and informed identification method which is used in different fields due to its uniqueness of the countless behavioural and physiological traits like hand geometry, finger prints, iris recognition, face recognition, handwriting, voice recognition, etc. Iris recognition system is widely being used as it has inherently distinctive patterns that provide a robust method for the identification purpose. Different nations have already started to use biometric recognition system for the identification purposes including patient identification, border security, etc. In this review paper, different steps that are involved in Iris Recognition system are defined and evaluation of different Iris Recognition methods used by different researchers for each recognition step is done as well.
KEYWORDS:
Biometric; recognition; identification; uniqueness
Copy the following to cite this article:
Mattoo I. A, Agarwal P. Iris Biometric Modality: A Review. Orient.J. Comp. Sci. and Technol;10(2)
|
Introduction
The difficulty with the traditional use of passwords, usernames or to possess tokens like (identity cards, keys etc.) for the security purpose is that they can easily be evaded by hackers and the rogue employees. Due to these apparent security issues related to use of passwords as security measures, biometric recognition system is becoming the standard model when trying to guard access to critical data. In the biometric world, identification of human being deals with their physiological and /or behavioural characteristics [1]. A biometric recognition framework works by first capturing an image for example, capturinga electronic picture of an iris to be exploited as a part of iris acknowledgment or a recording a sound flag that can be used as a part of voice acknowledgment. The examples may then be refined in order to obtain the most specific features and the irrelevant information is reduced. Then the obtained specimen is changed into a biometric format by using different kinds of recognition methods. Iris recognition is considered as one of the most accurate and protected biometric modality [2].Biometric system can be categorized into two different systems which are defined below: –
Verification(authentication) – One to One: Biometric system can be used to validate a person’s identity. For example, one can be granted access to a bank account at an ATM by using retinal scan or one can grant physical access to a protected area in a building by using finger scans [2].
Identification system – One to Many: Biometrics can also be used to govern a person’s identity even without his consent or knowledge. For example, scanning a crowd with a camera and using face recognition technology, one can determine matches against a known database.
First of all this review paper gives the brief introduction about the biometric recognition technology. Section II illustrates the literature survey and the work done in the related field. Then the section III defines the various steps in the iris recognition system. Section IV briefly defines the requirements for the implementation of system. The last section i.e, section V gives the conclusion of the whole paper.
Related work
Tremendous amount of work has already been done in the field of biometric iris recognition and some of the research articles discussed in this section.
Daouk et al. [3] proposed iris recognition schemes which involve a combination of Canny Edge Detection scheme and a Circular Hough Transform, to detect the boundaries in an iris image. Then Haar wavelet is used in order to find out the deterministic patterns in a person’s iris in the form of a feature vector. Wavelet tree was used for image mapping and the average correct recognition rate is about 93%.
Zhaofeng He, Tieniu Tan [4] has given a study on the separation of picture of iris that only focusses on the basic components and rejects the undesirable elements.
Azizi et al. [5] proposed a work which deals with the using of features extraction and subset selection. Iris features were being extracted using contourlet transform. Support Vector Machine (SVM) has been used for matching the iris templates. Gabor filter and Haar wavelet were used in this proposed work for coding.CASIA image database was used to check the performance of the proposed system.
Khattab M. Ali Alheeti proposed an iris recognition system using wavelet and equalization techniques. Different types of edge detection methods were being implemented in his work like sobel, canny, prewitt scheme used in his work. The proposed system provides sufficient amount of results through different types of iris images [6].
Xu et al. [7] proposed an improved iris recognition algorithm which deals with the detection of eyelashes and eyelids. The main reason for detecting eyelids and eyelashes is that because of the presence of these, affects the iris image as well as it produces noise that results in the performance degradation of system. For enhancement of iris image in this proposed, subtraction of background was done. Histogram equalization and viener was used for filtering. For the detection of eyelids/eyelashes summary derivate was used.
Bhawna chouhan and et al. proposed a biometric system based on instinctive identification of a person based on his/her unique characteristic or attribute possessed by the individual. The proposed system focuses on image segmentation and feature extraction for iris recognition process. The Canny Edge Detector is used for edge detection and is one of the most commonly used image processing tool, detecting the edges in a very robust manner. Even an effective feature extraction method would not be able to obtain useful information from an iris image if the image is not properly segmented [8].
An algorithm developed by Noh [9], et al., does a comparison on different types of feature extraction techniques includingHaar Wavelet, Gabor wavelets, DAUB4 wavelets, Multiresolution ICA(M-ICA), and Independent Component Analysis (ICA). ICA is an unsupervised learning algorithm using high-order statistics, and M-ICA is anew method of feature extraction, introduced by these authors. The Fisher Discrimination Ratiohas been used as a comparison tool.
Iris Recognition System
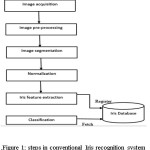
The iris recognition technology has following basic technological steps which are defined as follows: –
- Image acquisition
- Pre-processing of image
- Image Segmentationand normalization
- Feature Encoding
- Classification
Figure 1 shows the various steps present in iris recognition system.
Image Acquisition/Capturing
The first stage in the iris recognition system is acquisition or capturing and its one of the major challenges so we need the specially designed cameras. Iris and pupil part in an image must be clearly visible. The acquisition distance for capturing is up to 2 to 3 feet. Also, there are a number of free databases available on the internet and image can be taken from them, for the testing purpose and some well-known database is the CASIA Iris Image database granted by the Chinese Academy of Science. There are some other database like, UBIRIS database, LEI and the UPOL database.
Pre-processing of image
Pre-processing of images usually involves the eliminating of less-frequency background noise, and normalizing the intensity of the images, eliminating the reflections, and concealing the portions of images. Image reprocessing is the technique of enhancing data images prior to computational processing. Pre-processing involves various steps such as boundary detection, iris detection, eyelid detection, pupil detection and removal and normalization. Pre-processing of the images can be done using thresholding and by various morphological operations.
Iris Segmentation and Normalization
The goal of segmentation is to change or simplify an image into something that is easier to understand and analyse. Image segmentation is mainly used to trace objects and boundaries in images and is also required to separate and ignore the artifacts as well as locating the spherical iris section. The inner and the outer margins of the iris are calculated. The segmentation operation also helps to improves the contrast between each eyes regions, which possibly will ease the segmentation task. There are various algorithms and techniques developed for image segmentation and these segmentation techniques must be joined with a field’s specific knowledge so that the segmentation problem can be easily solved in the required field. Some of the segmentation techniques are as follows: – a) Thresholding method, b) clustering method, c) compression based methods, d) histogram based methods, e) region growing methods, etc.
Normalization Stage
This stage is employed basically for converting the circular iris into rectangular iris. It transforms the Iris from Cartesian to polar coordinates to make it constant and persistent in nature against the effect of variation in size of the pupil. Daugman’s Rubber Sheet model is commonly used for the unwrapping of Iris.
Feature Coding
Feature extraction helps to remove redundancy from data and further helps in simplifying the classification and learning steps. Feature extraction also helps in dimensionality reduction thus increasing the amount of useful information in original image. The significant features of the iris must be only encoded so that comparisons between the templates can be made correctly. the two important problems must be clarified which are feature extraction and feature selection,before the of construction feature extraction procedure. Feature extraction implies that which technique shall be used to extract features from the image. On the other hand, the feature selection, helps in selecting the most relevant features to improve the classification accuracy. Some of the common feature extraction techniques include Haar Wavelets, Log Gabor filter Histogram of Oriented Gradients (HOG), Speeded Up Robust Features (SURF), Local Binary Patterns (LBP), and color histograms.
Classification Techniques
The Image classification investigates the numerical properties of various image features and then arranges data into categories. The classification algorithms usually have two stages of processing: training phase and the testing phase. In the training phase, distinctive properties of an image features are isolated and, based on these, training class, is created. In the following testing phase, these features are used to classify image features.The classification technique of an iris biometric recognition system is used for matching two iris templates [11]. There are different classification techniques that will be used on the appropriate data sets. Some methods of the classification techniques are as: – Linear and Discriminant Analysis, Neural Network, SVM, DAG, BMMA, Fuzzy Tree, and K Nearest Neighbour.
Requirement for implementation
This proposed method is tested on CASIA image database from Institute of Chinese Academy of Science (CASIA), the procedure was verified and shall be implemented using MATLAB R2016a.
Conclusion
Iris scanning biometric modality measures the distinctive patterns in the circle of your eye to confirm and validate the identity of an individual. Iris scanning is contactless making it more hygienic than other biometric modalities, and it isfast and famous for its accuracy, only a glance of the person is required for validating the identity of a person. This paper provides a general review on various prevailing methods proposed by different researchers for iris recognition. The image of the iris is acquired then pre-processing of the images is done using thresholding and different morphological operations. Segmentation of the image can be done using various segmentation algorithm. And finally the feature extraction and classification is employed using different techniques. Iris recognition technology is able to give highly accurate results for the identification. The algorithms are generally executed into four steps namely, pre-processing, segmentation and normalization, feature extraction and classification.
References
- R.P. Wilders, 1997. “Iris Recognition: An Emerging Biometric Technology”, Proceeding of the IEEE, Vol. 85, No. 9, pp. 1348-1363.
CrossRef
- Ishpreet Singh Virk et.al, 2012. “Biometric Authentication System: Tools and Techniques” in International Journal of Computer Application, Vol. 2, ISSN 2250-1797,pp 150-163.
- C.H. Daouk et al.,2002. “IRIS RECOGNITION”, Proceeding of the IEEE ISSPIT, Marrakesh, pp. 558-562.
- Zhaofeng, H., Tieniu, T., Zhenan, S., Xianchao, Q., 2008. “Towards Accurate and Fast Iris Segmentation for Iris Biometrics”, IEEE Transactions On Pattern Analysis and Machine Intelligence, PP. 1-14. .
- Azizi,A., Pourreza,H.,R., 2009. “Efficient IRIS Recognition through Improvement of Feature Extraction and subset Selection” inInternational Journal of Computer Science and Information Security, Vol. 2, No. 1.
- Alheeti,K., M., A., 2011. “Biometrics Iris Recognition Based On Hybrid Technique” in International Journal on Soft Computing(IJSC), Vol.2, No.4, pp 1-9.
- Xu, G., Zhang,Z., Ma, Y., 2006. “Improving The Performance Of Iris Recognition System Using Eyelids And Eyelashes Detection and Iris Image Enhancement”, Proceeding of the IEEE International Conference on Cognitive Informatics, pp. 871-876.
- Chouhan,B., Shukla,S.,2011.” Iris Recognition System using canny edge detection for Biometric Identification”, Interrnational Journal of engineering Sciences and Technology (IJEST), ISSN: 09755462 Vol. 3 No. 1, pp 31-35.
- S. Noh, K.Pae, C. Lee, J. Kim, 2002. “Multiresolution independent component analysis for iris identification” in the proceedings of “The 2002 International Technical Conference on Circuits/Systems,Computers and Communications”, Phuket, Thailand.
- Gupta, A., Mahajan, S., 2015, “An Efficient Iris Recognition System using DCT Transform based on Feed Forward Neural Networks” in International Journal of Software & Hardware Research in Engineering,Vol 3, ISSN-2347-4890.
- Sharma et al., International Journal of Advanced Research in Computer Science and Software Engineering 4(9),

This work is licensed under a Creative Commons Attribution 4.0 International License.